SNCF Questions – Part 2
Question 1
Which CLI command is used to control special handling of ClientHello messages?
A. system support ssl-client-hello-tuning
B. system support ssl-client-hello-display
C. system support ssl-client-hello-force-reset
D. system support ssl-client-hello-reset
Answer: A
Explanation
In fact there is no correct answer in this question, the correct answer should be “system support ssl-client-hello-enabled” which controls all special handling of ClientHello messages.
But we have to choose one best answer then “system support ssl-client-hello-tuning” is the best choice. It allows you to refine how the managed device modifies ClientHello messages during SSL handshakes. This command tunes the default lists of cipher suites, elliptic curves, and extensions that the system allows in ClientHello messages.
Question 2
Which command is typed at the CLI on the primary Cisco FTD unit to temporarily stop running high-availability?
A. configure high-availability resume
B. configure high-availability disable
C. system support network-options
D. configure high-availability suspend
Answer: D
Explanation
We only want to “temporarily” stop so the keyword must be “suspend”, not “disable” (which breaks the high availability connection permanently).
Question 3
Which command must be run to generate troubleshooting files on an FTD?
A. system support view-files
B. sudo sf_troubleshoot.pl
C. system generate-troubleshoot all
D. show tech-support
Answer: C
Question 4
When do you need the file-size command option during troubleshooting with packet capture?
A. when capture packets are less than 16 MB
B. when capture packets are restricted from the secondary memory
C. when capture packets exceed 10 GB
D. when capture packets exceed 32 MB
Answer: D
Question 5
What is a functionality of port objects in Cisco FMC?
A. to mix transport protocols when setting both source and destination port conditions in a rule
B. to represent protocols other than TCP, UDP, and ICMP
C. to represent all protocols in the same way
D. to add any protocol other than TCP or UDP for source port conditions in access control rules.
Answer: B
Question 6
Within Cisco Firepower Management Center, where does a user add or modify widgets?
A. dashboard
B. reporting
C. context explorer
D. summary tool
Answer: A
Question 7
A network engineer is configuring URL Filtering on Firepower Threat Defense. Which two port requirements on the Firepower Management Center must be validated to allow communication with the cloud service? (Choose two)
A. outbound port TCP/443
B. inbound port TCP/80
C. outbound port TCP/8080
D. inbound port TCP/443
E. outbound port TCP/80
Answer: A E
Question 8
What is a behavior of a Cisco FMC database purge?
A. User login and history data are removed from the database if the User Activity check box is selected.
B. Data can be recovered from the device.
C. The appropriate process is restarted.
D. The specified data is removed from Cisco FMC and kept for two weeks.
Answer: C
Question 9
Which two packet captures does the FTD LINA engine support? (Choose two)
A. Layer 7 network ID
B. source IP
C. application ID
D. dynamic firewall importing
E. protocol
Answer: B E
Question 10
Which two features of Cisco AMP for Endpoints allow for an uploaded file to be blocked? (Choose two)
A. application blocking
B. simple custom detection
C. file repository
D. exclusions
E. application whitelisting
Answer: A B
Question 11
Which action should you take when Cisco Threat Response notifies you that AMP has identified a file as malware?
A. Add the malicious file to the block list.
B. Send a snapshot to Cisco for technical support.
C. Forward the result of the investigation to an external threat-analysis engine.
D. Wait for Cisco Threat Response to automatically block the malware.
Answer: A
Question 12
What is a valid Cisco AMP file disposition?
A. non-malicious
B. malware
C. known-good
D. pristine
Answer: B
Question 13
In a Cisco AMP for Networks deployment, which disposition is returned if the cloud cannot be reached?
A. unavailable
B. unknown
C. clean
D. disconnected
Answer: A
Question 14
Which two remediation options are available when Cisco FMC is integrated with Cisco ISE? (Choose two)
A. dynamic null route configured
B. DHCP pool disablement
C. quarantine
D. port shutdown
E. host shutdown
Answer: CD
Question 15
Which connector is used to integrate Cisco ISE with Cisco FMC for Rapid Threat Containment?
A. pxGrid
B. FTD RTC
C. FMC RTC
D. ISEGrid
Answer: A
Question 16
What is the maximum SHA level of filtering that Threat intelligence Director supports?
A. SHA-1024
B. SHA-4096
C. SHA-512
D. SHA-256
Answer: D
Question 17
What is a result of enabling Cisco FTD clustering?
A. For the dynamic routing feature, if the master unit fails, the newly elected master unit maintains all existing connections.
B. integrated Routing and Bridging is supported on the master unit.
C. Site-to-site VPN functionality is limited to the master unit, and all VPN connections are dropped if the master unit fails.
D. All Firepower appliances can support Cisco FTD clustering.
Answer: C
Question 18
Which two conditions are necessary for high availability to function between two Cisco FTD devices? (Choose two)
A. The units must be the same version
B. Both devices can be part of a different group that must be in the same domain when configured within the FMC.
C. The units must be different models if they are part of the same series.
D. The units must be configured only for firewall routed mode.
E. The units must be the same model.
Answer: A E
Question 19
On the advanced tab under inline set properties, which allows interfaces to emulate a passive interface?
A. transparent inline mode
B. TAP mode
C. strict TCP enforcement
D. propagate link state
Answer: B
Question 20
Which two deployment types support high availability? (Choose two)
A. transparent
B. routed
C. clustered
D. intra-chassis multi-instance
E. virtual appliance in public cloud
Answer: A B
Question 21
What are 2 types or forms of suppression on a FirePower policy (or FTD)? (Choose two)
A. source
B. port
C. rule
D. protocol
E. application
Answer: A C
Question 22
Which protocol establishes network redundancy in a switched Firepower device deployment?
A. STP
B. HSRP
C. GLBP
D. VRRP
Answer: A
Question 23
Which Cisco Firepower Threat Defense, which two interface settings are required when configuring a routed interface? (Choose two)
A. Redundant interface
B. EtherChannel
C. Speed
D. Media Type
E. Duplex
Answer: CE
Question 24
Which two dynamic routing protocols are supported in Firepower Threat Defense without using FlexConfig? (Choose two)
A. EIGRP
B. OSPF
C. static routing
D. IS-IS
E. BGP
Answer: B E
Explanation
Both OSPF and BGP can be configured with Smart CLI without FlexConfig
Question 25
Which two OSPF routing features are configured in Cisco FMC and propagated to Cisco FTD? (Choose two)
A. OSPFv2 with iPv6 capabilities
B. virtual links
C. SHA authentication to OSPF packets
D. area boundary router type 1 LSA filtering
E. MD5 authentication to OSPF packets
Answer: B E
Question 26
What Software can be installed on the Cisco 4100 series appliance? (Choose two)
A. FTD
B. ASA
C. ASAv
D. FMC
Answer: A B
Question 27
Which two field can be used to create a new email alert within the Cisco Firepower Management center under Policies > Actions > Alerts tab? (Choose two)
A. Device
B. Source
C. Destination
D. From
E. Relay Host
Answer: D E
Question 28
When creating a report template, how can the results be limited to show only the activity of a specific subnet?
A. Create a custom search in Firepower Management Center and select it in each section of the report.
B. Add an input Parameter in the Advanced Settings of the report, and set the type to Network/IP.
C. Add a Table View section to the report with the Search field defined as the network in CIDR format.
D. Select IP Address as the X-Axis in each section of the report.
Answer: B
Question 29
What is the disadvantage of setting up a site-to-site VPN in a clustered-units environment?
A. VPN connections can be re-established only if the failed master unit recovers.
B. Smart License is required to maintain VPN connections simultaneously across all cluster units.
C. VPN connections must be re-established when a new master unit is elected.
D. Only established VPN connections are maintained when a new master unit is elected.
Answer: C
Question 30
Which two routing options are valid with Cisco Firepower Threat Defense? (Choose two)
A. BGPv6
B. ECMP with up to three equal cost paths across multiple interfaces
C. ECMP with up to three equal cost paths across a single interface
D. BGPv4 in transparent firewall mode
E. BGPv4 with nonstop forwarding
Answer: A C
Explanation
You can have up to 8 equal cost static or dynamic routes per interface (-> Answer C is correct). For example, you can configure multiple default routes on the outside interface that specify different gateways.
route for 0.0.0.0 0.0.0.0 through outside to 10.1.1.2 route for 0.0.0.0 0.0.0.0 through outside to 10.1.1.3 route for 0.0.0.0 0.0.0.0 through outside to 10.1.1.4
In this case, traffic is load-balanced on the outside interface between 10.1.1.2, 10.1.1.3, and 10.1.1.4. Traffic is distributed among the specified gateways based on an algorithm that hashes the source and destination IP addresses, incoming interface, protocol, source and destination ports.
Cisco Firepower Threat Defense Configuration Guide for Firepower Device Manager, Version 6.6
BGP can also be used for carrying routing information for IPv6 prefix over IPv6 networks. -> Answer A is correct.
Question 31
Which description of a correlation, policy configuration in the Cisco Firepower Management Center, is true?
A. Correlation policy priorities override whitelist priorities.
B. The system displays correlation policies that are created on all of the domains in a multidomain deployment.
C. You cannot add a host profile qualification to a correlation rule that is triggered by a malware event.
D. Deleting a response group deletes the responses of that group.
Answer: C
Question 32
Which two TCP ports can allow the Cisco Firepower Management Center to communication with FireAMP cloud for file disposition information? (Choose two)
A. 8080
B. 22
C. 8305
D. 32137
E. 443
Answer: D E
Question 33
Which object type supports object overrides?
A. time range
B. security group tag
C. network object
D. DNS server group
Answer: C
Question 34
Which Cisco Firepower rule action displays an HTTP warning page?
A. Monitor
B. Block
C. interactive Block
D. Allow with Warning
Answer: C
Question 35
What is the result of specifying of QoS rule that has a rate limit that is greater than the maximum throughput of an interface?
A. The rate-limiting rule is disabled.
B. Matching traffic is not rate limited.
C. The system rate-limits all traffic.
D. The system repeatedly generates warnings.
Answer: B
Question 36
Which Firepower feature allows users to configure bridges in routed mode and enables devices to perform Layer 2 switching between interfaces?
A. FlexConfig
B. BDI
C. SGT
D. iRB
Answer: D
Question 37
In which two places can thresholding settings be configured? (Choose two)
A. on each IPS rule
B. globally, within the network analysis policy
C. globally, per intrusion policy
D. on each access control rule
E. per preprocessor, within the network analysis policy
Answer: A C
Question 38
In which two ways do access control policies operate on a Cisco Firepower system? (Choose two)
A. Traffic inspection can be interrupted temporarily when configuration changes are deployed.
B. The system performs intrusion inspection followed by file inspection.
C. They can block traffic based on Security intelligence data.
D. File policies use an associated variable set to perform intrusion prevention.
E. The system performs a preliminary inspection on trusted traffic to validate that it matches the trusted parameters.
Answer: A C
Question 39
Which function is the primary function of Cisco AMP threat Grid?
A. automated email encryption
B. applying a real-time URI blacklist
C. automated malware analysis
D. monitoring network traffic
Answer: C
Question 40
Which are two features of Cisco Trust Anchor? (Choose two)
A. flood attack detection
B. secure boot
C. image signing
D. DDoS mitigation
E. SYN flood detection
Answer: B C
Explanation
Cisco Trust Anchor Technologies provide a highly secure foundation for certain Cisco products. They enable hardware and software authenticity assurance for supply chain trust and strong mitigation against a man-in-the-middle compromise of software and firmware. Trust Anchor capabilities include:
+ Image signing: Cryptographically signed images provide assurance that the firmware, BIOS, and other software are authentic and unmodified. As the system boots, the system’s software signatures are checked for integrity.
+ Secure Boot: Secure Boot anchors the boot sequence chain of trust to immutable hardware, mitigating threats against a system’s foundational state and the software that is to be loaded, regardless of a user’s privilege level. It provides layered protection against the persistence of illicitly modified firmware.
+ Trust Anchor module: A tamper-resistant, strong-cryptographic, single-chip solution provides hardware authenticity assurance to uniquely identify the product so that its origin can be confirmed to Cisco, providing assurance that the product is genuine.
Reference: https://www.secureitstore.com.au/Firepower-4110.asp
Question 41
Which two types of objects are reusable and supported by Cisco FMC? (Choose two)
A. dynamic key mapping objects that help link HTTP and HTTPS GET requests to Layer 7 application protocols.
B. reputation-based objects that represent Security intelligence feeds and lists, application filters based on category and reputation, and file lists
C. network-based objects that represent IP address and networks, port/protocols pairs, VLAN tags, security zones, and origin/destination country
D. network-based objects that represent FQDN mappings and networks, port/protocol pairs, VXLAN tags, security zones and origin/destination country
E. reputation-based objects, such as URL categories
Answer: B C
https://www.cisco.com/c/en/us/td/docs/security/firepower/620/configuration/guide/fpmc-config- guide-v62/
reusable_objects.html#ID-2243-00000414
Question 42
What is the benefit of selecting the trace option for packet capture?
A. The option indicates whether the packet was dropped or successful.
B. The option indicated whether the destination host responds through a different path.
C. The option limits the number of packets that are captured.
D. The option captures details of each packet.
Answer: A
Question 43
After deploying a network-monitoring tool to manage and monitor networking devices in your organization, you realize that you need to manually upload an MIB for the Cisco FMC. in which folder should you upload the MIB file?
A. /etc/sf/DCMIB.ALERT
B. /sf/etc/DCEALERT.MIB
C. /etc/sf/DCEALERT.MIB
D. system/etc/DCEALERT.MIB
Answer: C
https://www.cisco.com/c/en/us/td/docs/security/firesight/541/firepower-module-user-guide/asa- firepowermodule-user-guide-v541/Intrusion-External-Responses.pdf
Question 44
Which command is run at the CLI when logged in to an FTD unit, to determine whether the unit is managed locally or by a remote FMC server?
A. system generate-troubleshoot
B. show configuration session
C. show managers
D. show running-config | include manager
Answer: C
https://www.cisco.com/c/en/us/td/docs/security/firepower/command_ref/b_Command_Reference_for_Firepower_Threat_Defense/c_3.html
Question 45
Which command should be used on the Cisco FTD CLI to capture all the packets that hit an interface?
A. configure coredump packet-engine enable
B. capture-traffic
C. capture
D. capture WORD
Answer: D
Question 46
How many report templates does the Cisco Firepower Management Center support?
A. 20
B. 10
C. 5
D. unlimited
Answer: D
https://www.cisco.com/c/en/us/td/docs/security/firepower/60/configuration/guide/fpmc-config- guide-v60/Working_with_Reports.html
Question 47
Which action should be taken after editing an object that is used inside an access control policy?
A. Delete the existing object in use.
B. Refresh the Cisco FMC GUI for the access control policy.
C. Redeploy the updated configuration.
D. Create another rule using a different object name.
Answer: C
https://www.cisco.com/c/en/us/td/docs/security/firepower/630/configuration/guide/fpmc-config- guide-v63/reusable_objects.html
Question 48
Which function is the primary function of Cisco AMP threat Grid? (Choose two)
A. It analyzes copies of packets from the packet flow
B. The device is deployed in a passive configuration
C. If a rule is triggered the device generates an intrusion event.
D. The packet flow traverses the device
E. If a rule is triggered the device drops the packet
Answer: A C
Question 49
When using Cisco AMP for Networks, which feature copies a file to the Cisco AMP cloud for analysis?
A. Spero analysis
B. dynamic analysis
C. sandbox analysis
D. malware analysis
Answer: B
Question 50
Which report template field format is available in Cisco FMC?
A. box lever chart
B. arrow chart
C. bar chart
D. benchmark chart
Answer: C
https://www.cisco.com/c/en/us/td/docs/security/firepower/60/configuration/guide/fpmc-config- guide-v60/Working_with_Reports.html
Question 51
Which group within Cisco does the Threat Response team use for threat analysis and research?
A. Cisco Deep Analytics
B. OpenDNS Group
C. Cisco Network Response
D. Cisco Talos
Answer: D
https://www.cisco.com/c/en/us/products/security/threat-response.html#~benefits
Question 52
Which CLI command is used to generate firewall debug messages on a Cisco Firepower?
A. system support firewall-engine-debug
B. system support ssl-debug
C. system support platform
D. system support dump-table
Answer: A
https://www.cisco.com/c/en/us/support/docs/security/firepower-ngfw/212330-firepower- management-centerdisplay-acc.html
Question 53
Which command-line mode is supported from the Cisco Firepower Management Center CLI?
A. privileged
B. user
C. configuration
D. admin
Answer: C
https://www.cisco.com/c/en/us/td/docs/security/firepower/660/configuration/guide/fpmc-config- guide-v66/command_line_reference.pdf
Question 54
Which command is entered in the Cisco FMC CLI to generate a troubleshooting file?
A. show running-config
B. show tech-support chassis
C. system support diagnostic-cli
D. sudo sf_troubleshoot.pl
Answer: D
https://www.cisco.com/c/en/us/support/docs/security/sourcefire-defense-center/117663-technote- SourceFire-00.html
Question 55
With Cisco FTD integrated routing and bridging, which interface does the bridge group use to communicate with a routed interface?
A. switch virtual
B. bridge group member
C. bridge virtual
D. subinterface
Answer: C
Question 56
A network engineer is extending a user segment through an FTD device for traffic inspection without creating another IP subnet. How is this accomplished on an FTD device in routed mode?
A. by leveraging the ARP to direct traffic through the firewall
B. by assigning an inline set interface
C. by using a BVI and create a BVI IP address in the same subnet as the user segment
D. by bypassing protocol inspection by leveraging pre-filter rules
Answer: C
https://www.cisco.com/c/en/us/td/docs/security/firepower/640/configuration/guide/fpmc-config- guide-v64/
transparent_or_routed_firewall_mode_for_firepower_threat_defense.html
Question 57
Refer to the exhibit.

An engineer is analyzing the Attacks Risk Report and finds that there are over 300 instances of new operating systems being seen on the network. How is the Firepower configuration updated to protect these new operating systems?
A. Cisco Firepower automatically updates the policies.
B. The administrator requests a Remediation Recommendation Report from Cisco Firepower
C. Cisco Firepower gives recommendations to update the policies.
D. The administrator manually updates the policies.
Answer: C
Question 58
A security engineer is configuring an Access Control Policy for multiple branch locations. These locations share a common rule set and utilize a network object called INSIDE_NET which contains the locally significant internal network subnets at each location. What technique will retain the policy consistency at each location but allow only the locally significant network subnet within the applicable rules?
A. utilizing policy inheritance
B. utilizing a dynamic ACP that updates from Cisco Talos
C. creating a unique ACP per device
D. creating an ACP with an INSIDE_NET network object and object overrides
Answer: D
Question 59
An administrator is working on a migration from Cisco ASA to the Cisco FTD appliance and needs to test the rules without disrupting the traffic. Which policy type should be used to configure the ASA rules during this phase of the migration?
A. identity
B. intrusion
C. Access Control
D. Prefilter
Answer: D
https://www.cisco.com/c/en/us/td/docs/security/firepower/migration-tool/migration- guide/ASA2FTD-with-FPMigration-Tool/b_Migration_Guide_ASA2FTD_chapter_01011.html
Question 60
An engineer currently has a Cisco FTD device registered to the Cisco FMC and is assigned the address of 10 10.50.12. The organization is upgrading the addressing schemes and there is a requirement to convert the addresses to a format that provides an adequate amount of addresses on the network. What should the engineer do to ensure that the new addressing takes effect and can be used for the Cisco FTD to Cisco FMC connection?
A. Delete and reregister the device to Cisco FMC
B. Update the IP addresses from iFV4 to iPv6 without deleting the device from Cisco FMC
C. Format and reregister the device to Cisco FMC.
D. Cisco FMC does not support devices that use iPv4 IP addresses.
Answer: A
Question 61
After using Firepower for some time and learning about how it interacts with the network, an administrator is trying to correlate malicious activity with a user. Which widget should be configured to provide this visibility on the Cisco Firepower dashboards?
A. Custom Analysis
B. Current Status
C. Current Sessions
D. Correlation Events
Answer: A
Question 62
An administrator is attempting to remotely log into a switch in the data centre using SSH and is unable to connect. How does the administrator confirm that traffic is reaching the firewall?
A. by running Wireshark on the administrator’s PC
B. by performing a packet capture on the firewall.
C. by running a packet tracer on the firewall.
D. by attempting to access it from a different workstation.
Answer: B
https://www.cisco.com/c/en/us/support/docs/security/firepower-ngfw/212474-working-with- firepower-threatdefense-f.html#anc16
Question 63
An engineer is configuring a second Cisco FMC as a standby device but is unable to register with the active unit. What is causing this issue?
A. The primary FMC currently has devices connected to it.
B. The code versions running on the Cisco FMC devices are different
C. The licensing purchased does not include high availability
D. There is only 10 Mbps of bandwidth between the two devices.
Answer: B
https://www.cisco.com/c/en/us/td/docs/security/firepower/620/configuration/guide/fpmc-config- guide-v62/firepower_management_center_high_availability.html
Question 64
The event dashboard within the Cisco FMC has been inundated with low priority intrusion drop events, which are overshadowing high priority events. An engineer has been tasked with reviewing the policies and reducing the low priority events. Which action should be configured to accomplish this task?
A. generate events
B. drop packet
C. drop connection
D. drop and generate
Answer: B
Explanation
Within the packet view of an intrusion event, you can take several actions on the rule that triggered the event.
…
Drop packets — Click Set this rule to drop the triggering packet
Question 65
An engineer is implementing Cisco FTD in the network and is determining which Firepower mode to use. The organization needs to have multiple virtual Firepower devices working separately inside of the FTD appliance to provide traffic segmentation. Which deployment mode should be configured in the Cisco Firepower Management Console to support these requirements?
A. multiple deployment
B. single-context
C. single deployment
D. multi-instance
Answer: D
Question 66
An engineer is configuring a cisco FTD appliance in iPS-only mode and needs to utilize fail- to- wire interfaces. Which interface mode should be used to meet these requirements?
A. transparent
B. routed
C. passive
D. inline set
Answer: D
https://www.cisco.com/c/en/us/td/docs/security/firepower/630/configuration/guide/fpmc-config- guide-v63/inline_sets_and_passive_interfaces_for_firepower_threat_defense.html
Question 67
An engineer is troubleshooting application failures through a FTD deployment. While using the FMC CLI, it has been determined that the traffic in QoS not matching the desired policy. What should be done to correct this?
A. Use the system support firewall-engine-debug command to determine which rules the traffic matching and modify the rule accordingly
B. Use the system support application-identification-debug command to determine which rules the traffic matching and modify the rule accordingly
C. Use the system support firewall-engine-dump-user-f density-data command to change the policy and allow the application through the firewall.
D. Use the system support network-options command to fine tune the policy.
Answer: A
Question 68
An engineer has been asked to show application usages automatically on a monthly basis and send the information to management. What mechanism should be used to accomplish this task?
A. event viewer
B. reports
C. dashboards
D. context explorer
Answer: B
Question 69
An organization has noticed that malware was downloaded from a website that does not currently have a known bad reputation. How will this issue be addresses globally in the quickest way possible and with the least amount of impact?
A. by denying outbound web access
B. Cisco Talos will automatically update the policies.
C. by isolating the endpoint
D. by creating a URL object in the policy to block the website
Answer: D
Question 70
An organization has implemented Cisco Firepower without IPS capabilities and now wants to enable inspection for their traffic. They need to be able to detect protocol anomalies and utilize the Snort rule sets to detect malicious behavior. How is this accomplished?
A. Modify the network discovery policy to detect new hosts to inspect.
B. Modify the access control policy to redirect interesting traffic to the engine.
C. Modify the intrusion policy to determine the minimum severity of an event to inspect.
D. Modify the network analysis policy to process the packets for inspection.
Answer: B
https://www.cisco.com/c/en/us/td/docs/security/firepower/670/fdm/fptd-fdm-config-guide-670/fptdfdmintrusion.html
Question 71
A hospital network needs to upgrade their Cisco FMC managed devices and needs to ensure that a disaster recovery process is in place. What must be done in order to minimize downtime on the network?
A. Configure a second circuit to an ISP for added redundancy
B. Keep a copy of the current configuration to use as backup
C. Configure the Cisco FMCs for failover
D. Configure the Cisco FMC managed devices for clustering.
Answer: B
Question 72
An engineer is monitoring network traffic from their sales and product development departments, which are on two separate networks. What must be configured in order to maintain data privacy for both departments?
A. Use a dedicated IPS inline set for each department to maintain traffic separation
B. Use 802 1Q mime set Trunk interfaces with VLANs to maintain logical traffic separation
C. Use passive IDS ports for both departments
D. Use one pair of inline set in TAP mode for both departments
Answer: A
https://www.cisco.com/c/en/us/td/docs/security/firepower/640/configuration/guide/fpmc-config- guide-v64/inline_sets_and_passive_interfaces_for_firepower_threat_defense.html
Question 73
A Cisco FTD device is running in transparent firewall mode with a VTEP bridge group member ingress interface. What must be considered by an engineer tasked with specifying a destination MAC address for a packet trace?
A. The destination MAC address is optional if a VLAN ID value is entered
B. Only the UDP packet type is supported
C. The output format option for the packet logs unavailable
D. The VLAN ID and destination MAC address are optional
Answer: A
Explanation
https://www.cisco.com/c/en/us/td/docs/security/firepower/620/configuration/guide/fpmc-config- guide-v62/troubleshooting_the_system.html
Question 74
What is a characteristic of bridge groups on a Cisco FTD?
A. in routed firewall mode, routing between bridge groups must pass through a routed interface.
B. in routed firewall mode, routing between bridge groups is supported.
C. in transparent firewall mode, routing between bridge groups is supported
D. Routing between bridge groups is achieved only with a router-on-a-stick configuration on a connected router
Answer: C (?)
Explanation
A bridge group is a group of interfaces that the FTD device bridges instead of routes. Bridge groups are only supported in Transparent Firewall Mode.
But in FTD v7.0 Cisco says:
A bridge group is a group of interfaces that the FTD device bridges instead of routes. Bridge groups are supported in both transparent and routed firewall mode
We are not sure which version of FTD this question wants to ask.
Question 75 (duplicated so we removed it)
Question 76
An organization has a compliance requirement to protect servers from clients, however, the clients and servers all reside on the same Layer 3 network. Without readdressing IP subnets for clients or servers, how is segmentation achieved?
A. Deploy a firewall in transparent mode between the clients and servers.
B. Change the IP addresses of the clients, while remaining on the same subnet.
C. Deploy a firewall in routed mode between the clients and servers
D. Change the IP addresses of the servers, while remaining on the same subnet
Answer: A
Question 77
In a multi-tenant deployment where multiple domains are in use. Which update should be applied outside of the Global Domain?
A. minor upgrade
B. local import of intrusion rules
C. Cisco Geolocation Database
D. local import of major upgrade
Answer: B
Question 78
A mid-sized company is experiencing higher network bandwidth utilization due to a recent acquisition. The network operations team is asked to scale up their one Cisco FTD appliance deployment to higher capacities due to the increased network bandwidth. Which design option should be used to accomplish this goal?
A. Deploy multiple Cisco FTD appliances in firewall clustering mode to increase performance.
B. Deploy multiple Cisco FTD appliances using VPN load-balancing to scale performance.
C. Deploy multiple Cisco FTD HA pairs to increase performance
D. Deploy multiple Cisco FTD HA pairs in clustering mode to increase performance
Answer: A
Explanation
https://www.cisco.com/c/en/us/td/docs/security/firepower/fxos/clustering/ftd-clustersolution.html#concept_C8502505F840451C9E600F1EED9BC18E
Question 79
An organization has seen a lot of traffic congestion on their links going out to the internet. There is a Cisco Firepower device that processes all of the traffic going to the internet prior to leaving the enterprise. How is the congestion alleviated so that legitimate business traffic reaches the destination?
A. Create a flexconfig policy to use WCCP for application aware bandwidth limiting
B. Create a VPN policy so that direct tunnels are established to the business applications
C. Create a NAT policy so that the Cisco Firepower device does not have to translate as many addresses
D. Create a QoS policy rate-limiting high bandwidth applications
Answer: D
Question 80
An engineer configures an access control rule that deploys file policy configurations to security zone or tunnel zones, and it causes the device to restart. What is the reason for the restart?
A. Source or destination security zones in the access control rule matches the security zones that are associated with interfaces on the target devices.
B. The source tunnel zone in the rule does not match a tunnel zone that is assigned to a tunnel rule in the destination policy.
C. Source or destination security zones in the source tunnel zone do not match the security zones that are associated with interfaces on the target devices.
D. The source tunnel zone in the rule does not match a tunnel zone that is assigned to a tunnel rule in the source policy.
Answer: A
https://www.cisco.com/c/en/us/td/docs/security/firepower/623/configuration/guide/fpmc-config- guide-v623/policy_management.html
Question 81
An engineer is attempting to create a new dashboard within the Cisco FMC to have a single view with widgets from many of the other dashboards. The goal is to have a mixture of threat and security related widgets along with Cisco Firepower device health information. Which two widgets must be configured to provide this information? (Choose two)
A. intrusion Events
B. Correlation information
C. Appliance Status
D. Current Sessions
E. Network Compliance
Answer: AC
https://www.cisco.com/c/en/us/td/docs/security/firepower/640/configuration/guide/fpmc-config- guide-v64/dashboards.html#ID-2206-00000283
Question 82
An organization is setting up two new Cisco FTD devices to replace their current firewalls and cannot have any network downtime. During the setup process, the synchronization between the two devices is failing. What action is needed to resolve this issue?
A. Confirm that both devices have the same port-channel numbering
B. Confirm that both devices are running the same software version
C. Confirm that both devices are configured with the same types of interfaces
D. Confirm that both devices have the same flash memory sizes
Answer: D
https://www.cisco.com/c/en/us/td/docs/security/firepower/623/configuration/guide/fpmc-config- guide-v623/firepower_threat_defense_high_availability.html#Cisco_Reference.dita_cc8821d8- a5a5-49c0-97fddc9b6f7dbad2
Question 83
There is an increased amount of traffic on the network and for compliance reasons, management needs visibility into the encrypted traffic. What is a result of enabling TLS/SSL decryption to allow this visibility?
A. it prompts the need for a corporate managed certificate
B. it has minimal performance impact
C. it is not subject to any Privacy regulations
D. it will fail if certificate pinning is not enforced
Answer: A
Question 84
An organization wants to secure traffic from their branch office to the headquarter building using Cisco Firepower devices, They want to ensure that their Cisco Firepower devices are not wasting resources on inspecting the VPN traffic. What must be done to meet these requirements?
A. Configure the Cisco Firepower devices to ignore the VPN traffic using prefilter policies
B. Enable a flexconfig policy to re-classify VPN traffic so that it no longer appears as interesting traffic
C. Configure the Cisco Firepower devices to bypass the access control policies for VPN traffic.
D. Tune the intrusion policies in order to allow the VPN traffic through without inspection
Answer: C
Explanation
Question 85
A network administrator is seeing an unknown verdict for a file detected by Cisco FTD. Which malware policy configuration option must be selected in order to further analyse the file in the Talos cloud?
A. Spero analysis
B. Malware analysis
C. Dynamic analysis
D. Sandbox analysis
Answer: C
Question 86
An engineer has been tasked with providing disaster recovery for an organization’s primary Cisco FMC. What must be done on the primary and secondary Cisco FMCs to ensure that a copy of the original corporate policy is available if the primary Cisco FMC fails?
A. Configure high-availability in both the primary and secondary Cisco FMCs
B. Connect the primary and secondary Cisco FMC devices with Category 6 cables of not more than 10 meters in length.
C. Place the active Cisco FMC device on the same trusted management network as the standby device
D. Restore the primary Cisco FMC backup configuration to the secondary Cisco FMC device when the primary device fails
Answer: A
https://www.cisco.com/c/en/us/td/docs/security/firepower/620/configuration/guide/fpmc-config- guide-v62/firepower_management_center_high_availability.html
Question 87
Refer to the exhibit.
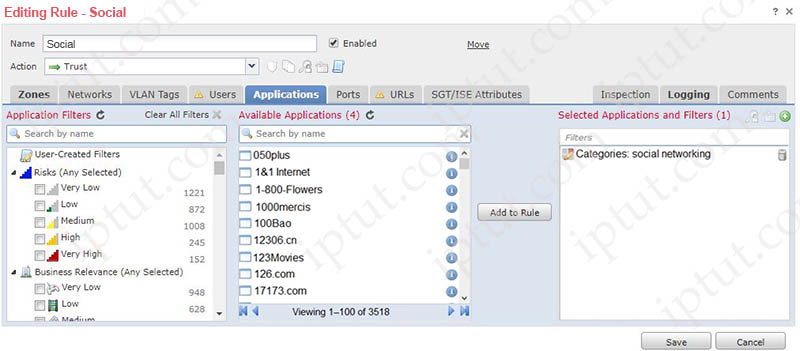
An organization has an access control rule with the intention of sending all social media traffic for inspection. After using the rule for some time, the administrator notices that the traffic is not being inspected, but is being automatically allowed. What must be done to address this issue?
A. Modify the selected application within the rule
B. Change the intrusion policy to connectivity over security.
C. Modify the rule action from trust to allow
D. Add the social network URLs to the block list
Answer: C
Question 88
A user within an organization opened a malicious file on a workstation which in turn caused a ransomware attack on the network. What should be configured within the Cisco FMC to ensure the file is tested for viruses on a sandbox system?
A. Capacity handling
B. Local malware analysis
C. Spere analysis
D. Dynamic analysis
Answer: D
https://www.cisco.com/c/en/us/td/docs/security/firepower/623/configuration/guide/fpmc-config- guide-v623/file_policies_and_advanced_malware_protection.html#ID-2199-000005d8
Question 89
An engineer configures a network discovery policy on Cisco FMC. Upon configuration, it is noticed that excessive and misleading events filing the database and overloading the Cisco FMC. A monitored NAT device is executing multiple updates of its operating system in a short period of time. What configuration change must be made to alleviate this issue?
A. Leave default networks.
B. Change the method to TCP/SYN.
C. increase the number of entries on the NAT device.
D. Exclude load balancers and NAT devices.
Answer: D
https://www.cisco.com/c/en/us/td/docs/security/firepower/60/configuration/guide/fpmc-config- guide-v60/Network_Discovery_Policies.html
Question 90
A network administrator is configuring SNORT inspection policies and is seeing failed deployment messages in Cisco FMC. What information should the administrator generate for Cisco TAC to help troubleshoot?
A. A Troubleshoot” file for the device in question.
B. A “show tech” file for the device in question
C. A “show tech” for the Cisco FMC.
D. A “troubleshoot” file for the Cisco FMC
Answer: D
https://www.cisco.com/c/en/us/td/docs/security/firepower/620/configuration/guide/fpmc-config- guide-v62/troubleshooting_the_system.html
Question 91
A network engineer is receiving reports of users randomly getting disconnected from their corporate applications which traverses the data center FTD appliance Network monitoring tools show that the FTD appliance utilization is peaking above 90% of total capacity. What must be done in order to further analyze this issue?
A. Use the Packet Export feature to save data onto external drives
B. Use the Packet Capture feature to collect real-time network traffic
C. Use the Packet Tracer feature for traffic policy analysis
D. Use the Packet Analysis feature for capturing network data
Answer: B
https://www.cisco.com/c/en/us/support/docs/security/firepower-ngfw/212474-working-with- firepower-threatdefense-f.html
Question 92
IT management is asking the network engineer to provide high-level summary statistics of the Cisco FTD appliance in the network. The business is approaching a peak season so the need to maintain business uptime is high. Which report type should be used to gather this information?
A. Malware Report
B. Standard Report
C. SNMP Report
D. Risk Report
Answer: D
Question 93
Refer to the exhibit.
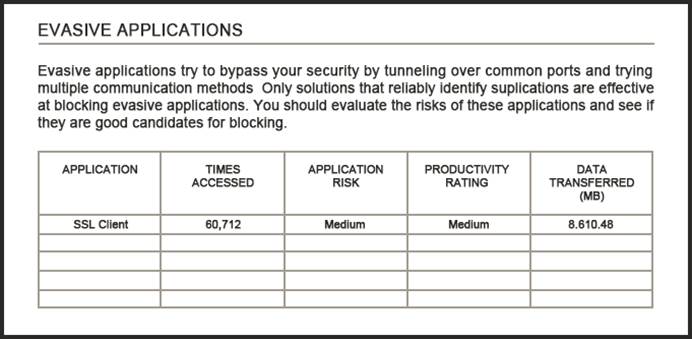
An administrator is looking at some of the reporting capabilities for Cisco Firepower and noticed this section of the Network Risk report showing a lot of SSL activity that cloud be used for evasion. Which action will mitigate this risk?
A. Use SSL decryption to analyze the packets.
B. Use encrypted traffic analytics to detect attacks
C. Use Cisco AMP for Endpoints to block all SSL connection
D. Use Cisco Tetration to track SSL connections to servers.
Answer: A
Question 94
An administrator is setting up Cisco Firepower to send data to the Cisco Stealthwatch appliances. The NetFlow_Set_Parameters object is already created, but NetFlow is not being sent to the flow collector. What must be done to prevent this from occurring?
A. Add the NetFlow_Send_Destination object to the configuration
B. Create a Security intelligence object to send the data to Cisco Stealthwatch
C. Create a service identifier to enable the NetFlow service
D. Add the NetFlow_Add_Destination object to the configuration
Answer: D
Question 95
With a recent summer time change, system logs are showing activity that occurred to be an hour behind real time. Which action should be taken to resolve this issue?
A. Manually adjust the time to the correct hour on all managed devices
B. Configure the system clock settings to use NTP with Daylight Savings checked
C. Manually adjust the time to the correct hour on the Cisco FMC.
D. Configure the system clock settings to use NTP
Answer: D
Question 96
Refer to the exhibit.
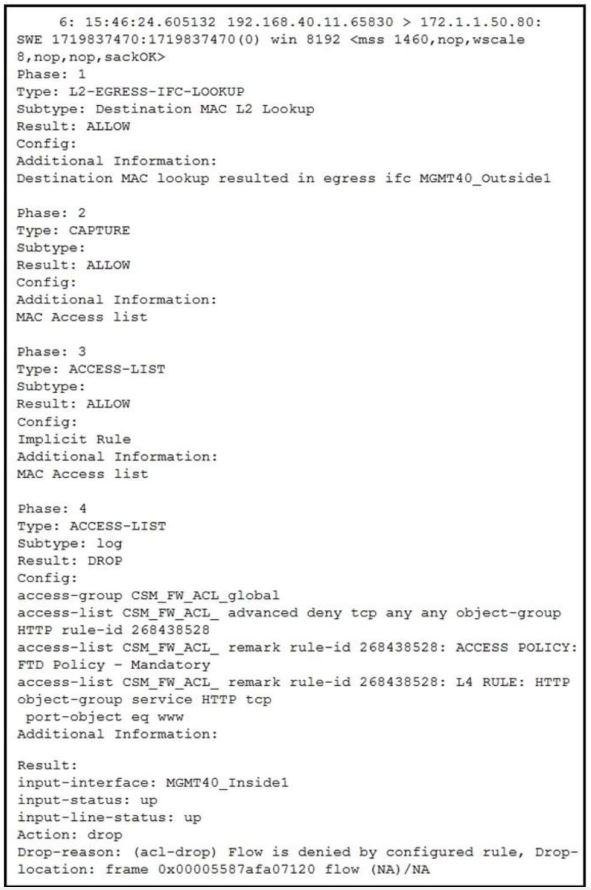
What must be done to fix access to this website while preventing the same communication to all other websites?
A. Create an intrusion policy rule to have Snort allow port 80 to only 172.1.1.50.
B. Create an intrusion policy rule to have Snort allow port 443 to only 172.1.1.50.
C. Create an access control policy rule to allow port 443 to only 172.1.1.50.
D. Create an access control policy rule to allow port 80 to only 172.1.1.50.
Answer: D
Question 97
A network administrator discovers that a user connected to a file server and downloaded a malware file. The Cisc FMC generated an alert for the malware event, however the user still remained connected. Which Cisco APM file rule action within the Cisco FMC must be set to resolve this issue?
A. Detect Files
B. Malware Cloud Lookup
C. Local Malware Analysis
D. Reset Connection
Answer: D
https://www.cisco.com/c/en/us/td/docs/security/firesight/541/firepower-module-user-guide/asa- firepowermodule-user-guide-v541/AMP-Config.pdf
Question 98
Which feature within the Cisco FMC web interface allows for detecting, analyzing and blocking malware in network traffic?
A. intrusion and file events
B. Cisco AMP for Endpoints
C. Cisco AMP for Networks
D. file policies
Answer: C
Question 99
Which license type is required on Cisco ISE to integrate with Cisco FMC pxGrid?
A. mobility
B. plus
C. base
D. apex
Answer: B
https://www.cisco.com/c/en/us/td/docs/security/ISE/1- 3/admin_guide/b_ISE_admin_guide_13/b_ISE_admin_guide_sample_chapter_0111.html#concept_DE1C38E055794B198ED352D1528B5182
Question 100
A network engineer wants to add a third-party threat feed into the Cisco FMC for enhanced threat detection Which action should be taken to accomplish this goal?
A. Enable Threat intelligence Director using STIX and TAXII
B. Enable Rapid Threat Containment using REST APis
C. Enable Threat intelligence Director using REST APis
D. Enable Rapid Threat Containment using STIX and TAXII
Answer: A
https://www.cisco.com/c/en/us/td/docs/security/firepower/623/configuration/guide/fpmc-config- guide-v623/cisco_threat_intelligence_director tid_.html
Question 101
What is a feature of Cisco AMP private cloud?
A. it supports anonymized retrieval of threat intelligence
B. it supports security intelligence filtering.
C. it disables direct connections to the public cloud.
D. it performs dynamic analysis
Answer: C
https://www.cisco.com/c/en/us/products/collateral/security/fireamp-private-cloud-virtual-appliance/datasheetc78-742267.html
Question 102
An engineer has been tasked with using Cisco FMC to determine if files being sent through the network are malware. Which two configuration tasks must be performed to achieve this file lookup? (Choose two)
A. The Cisco FMC needs to include a SSL decryption policy.
B. The Cisco FMC needs to connect to the Cisco AMP for Endpoints service.
C. The Cisco FMC needs to connect to the Cisco ThreatGrid service directly for sandboxing.
D. The Cisco FMC needs to connect with the FireAMP Cloud.
E. The Cisco FMC needs to include a file inspection policy for malware lookup.
Answer: DE
https://www.cisco.com/c/en/us/td/docs/security/firepower/60/configuration/guide/fpmc-config- guide-v60/Reference_a_wrapper_Chapter_topic_here.html#ID-2193-00000296
Question 103
An engineer is restoring a Cisco FTD configuration from a remote backup using the command restore remote-manager-backup location 1.1.1.1 admin /volume/home/admin BACKUP_Cisc394602314.zip on a Cisco FMG. After connecting to the repository, an error occurred that prevents the FTD device from accepting the backup file.. What is the problem?
A. The backup file is not in .cfg format.
B. The backup file is too large for the Cisco FTD device
C. The backup file extension was changed from tar to zip
D. The backup file was not enabled prior to being applied
Answer: C
Question 104
A network engineer is logged into the Cisco AMP for Endpoints console and sees a malicious verdict for an identified SHA-256 hash. Which configuration is needed to mitigate this threat?
A. Add the hash to the simple custom detection list.
B. Use regular expressions to block the malicious file.
C. Enable a personal firewall in the infected endpoint.
D. Add the hash from the infected endpoint to the network block list.
Answer: A
Question 105
An organization has a Cisco IPS running in inline mode and is inspecting traffic for malicious activity. When traffic is received by the Cisco IRS, if it is not dropped, how does the traffic get to its destination?
A. it is retransmitted from the Cisco IPS inline set.
B. The packets are duplicated and a copy is sent to the destination.
C. it is transmitted out of the Cisco IPS outside interface.
D. it is routed back to the Cisco ASA interfaces for transmission.
Answer: A
Question 106
A network administrator is concerned about the high number of malware files affecting users’ machines. What must be done within the access control policy in Cisco FMC to address this concern?
A. Create an intrusion policy and set the access control policy to block.
B. Create an intrusion policy and set the access control policy to allow.
C. Create a file policy and set the access control policy to allow.
D. Create a file policy and set the access control policy to block.
Answer: C
Question 107
An engineer is investigating connectivity problems on Cisco Firepower that is using service group tags. Specific devices are not being tagged correctly, which is preventing clients from using the proper policies when going through the firewall How is this issue resolved?
A. Use traceroute with advanced options.
B. Use Wireshark with an IP subnet filter.
C. Use a packet capture with match criteria.
D. Use a packet sniffer with correct filtering
Answer: C
Question 108
An organization must be able to ingest NetFlow traffic from their Cisco FTD device to Cisco Stealthwatch for behavioral analysis. What must be configured on the Cisco FTD to meet this requirement?
A. flexconfig object for NetFlow
B. interface object to export NetFlow
C. security intelligence object for NetFlow
D. variable set object for NetFlow
Answer: A
Question 109
An engineer is tasked with deploying an internal perimeter firewall that will support multiple DMZs Each DMZ has a unique private IP subnet range. How is this requirement satisfied?
A. Deploy the firewall in transparent mode with access control policies.
B. Deploy the firewall in routed mode with access control policies.
C. Deploy the firewall in routed mode with NAT configured.
D. Deploy the firewall in transparent mode with NAT configured.
Answer: B
Question 110
An engineer must build redundancy into the network and traffic must continuously flow if a redundant switch in
front of the firewall goes down. What must be configured to accomplish this task?
A. redundant interfaces on the firewall cluster mode and switches
B. redundant interfaces on the firewall noncluster mode and switches
C. vPC on the switches to the interface mode on the firewall duster
D. vPC on the switches to the span EtherChannel on the firewall cluster
Answer: D
Question 111
What is the advantage of having Cisco Firepower devices send events to Cisco Threat Response via the security services exchange portal directly as opposed to using syslog?
A. All types of Cisco Firepower devices are supported.
B. An on-premises proxy server does not need to be set up and maintained.
C. Cisco Firepower devices do not need to be connected to the internet.
D. Supports all devices that are running supported versions of Cisco Firepower.
Answer: B
Question 112
An engineer must configure high availability for the Cisco Firepower devices. The current network topology does not allow for two devices to pass traffic concurrently. How must the devices be implemented in this environment?
A. in active/active mode
B. in a cluster span EtherChannel
C. in active/passive mode
D. in cluster interface mode
Answer: C
Question 113
When deploying a Cisco ASA Firepower module, an organization wants to evaluate the contents of the traffic without affecting the network. it is currently configured to have more than one instance of the same device on the physical appliance. Which deployment mode meets the needs of the organization?
A. inline tap monitor-only mode
B. passive monitor-only mode
C. passive tap monitor-only mode
D. inline mode
Answer: A
Question 114
A network administrator notices that inspection has been interrupted on all non-managed interfaces of a device. What is the cause of this?
A. The value of the highest MTU assigned to any non-management interface was changed.
B. The value of the highest MSS assigned to any non-management interface was changed.
C. A passive interface was associated with a security zone.
D. Multiple inline interface pairs were added to the same inline interface.
Answer: A
Question 115
Which two conditions must be met to enable high availability between two Cisco FTD devices? (Choose two)
A. same flash memory size
B. same NTP configuration
C. same DHCP/PPoE configuration
D. same host name
E. same number of interfaces
Answer: BE
Question 116 (duplicated so we removed it)
Question 117
An engineer is building a new access control policy using Cisco FMC. The policy must inspect a unique IPS policy as well as log rule matching. Which action must be taken to meet these requirements?
A. Configure an IPS policy and enable per-rule logging.
B. Disable the default IPS policy and enable global logging.
C. Configure an IPS policy and enable global logging.
D. Disable the default IPS policy and enable per-rule logging.
Answer: A
Question 118
A network administrator needs to create a policy on Cisco Firepower to fast-path traffic to avoid Layer 7 inspection. The rate at which traffic is inspected must be optimized. What must be done to achieve this goal?
A. Enable the FXOS for multi-instance.
B. Configure a prefilter policy.
C. Configure modular policy framework.
D. Disable TCP inspection.
Answer: B
Question 119
A network engineer is tasked with minimising traffic interruption during peak traffic limes. When the SNORT inspection engine is overwhelmed, what must be configured to alleviate this issue?
A. Enable IPS inline link state propagation
B. Enable Pre-filter policies before the SNORT engine failure.
C. Set a Trust ALL access control policy.
D. Enable Automatic Application Bypass.
Answer: D
Question 120
A VPN user is unable to conned lo web resources behind the Cisco FTD device terminating the connection. While troubleshooting, the network administrator determines that the DNS responses are not getting through the Cisco FTD. What must be done to address this issue while still utilizing Snort IPS rules?
A. Uncheck the “Drop when inline” box in the intrusion policy to allow the traffic.
B. Modify the Snort rules to allow legitimate DNS traffic to the VPN users.
C. Disable the intrusion rule threshes to optimize the Snort processing.
D. Decrypt the packet after the VPN flow so the DNS queries are not inspected
Answer: B
Question 121
An organization is using a Cisco FTD and Cisco ISE to perform identity-based access controls. A network administrator is analyzing the Cisco FTD events and notices that unknown user traffic is being allowed through the firewall. How should this be addressed to block the traffic while allowing legitimate user traffic?
A. Modify the Cisco ISE authorization policy to deny this access to the user
B. Modify Cisco ISE to send only legitimate usernames to the Cisco FTD.
C. Add the unknown user in the Access Control Policy in Cisco FTD.
D. Add the unknown user in the Malware & File Policy in Cisco FTD.
Answer: C
Question 122
Within an organization’s high availability environment where both firewalls are passing traffic, traffic must be segmented based on which department it is destined for. Each department is situated on a different LAN. What must be configured to meet these requirements?
A. redundant interfaces
B. span EtherChannel clustering
C. high availability active/standby firewalls
D. multi-instance firewalls
Answer: D
Question 123
An engineer is configuring a Cisco IPS to protect the network and wants to test a policy before deploying it. A copy of each incoming packet needs to be monitored while traffic flow remains constant. Which IPS mode should be implemented to meet these requirements?
A. routed
B. passive
C. transparent
D. inline tap
Answer: D
Question 124
A network security engineer must replace a faulty Cisco FTD device in a high availability pair. Which action must be taken while replacing the faulty unit?
A. Ensure that the faulty Cisco FTD device remains registered to the Cisco FMC
B. Shut down the active Cisco FTD device before powering up the replacement unit
C. Shut down the Cisco FMC before powering up the replacement unit
D. Unregister the faulty Cisco FTD device from the Cisco FMC
Answer: A
Question 125
An administrator is optimizing the Cisco FTD rules to improve network performance, and wants to bypass inspection for certain traffic types to reduce the load on the Cisco FTD. Which policy must be configured to accomplish this goal?
A. intrusion
B. prefilter
C. URL filtering
D. identity
Answer: B
Question 126
A company is in the process of deploying intrusion prevention with Cisco FTDs managed by a Cisco FMC. An engineer must configure policies to detect potential intrusions but not block the suspicious traffic. Which action accomplishes this task?
A. Configure IPS mode when creating or editing a policy rule under the Cisco FMC intrusion tab in Access Policies section by checking the “Drop when inline” option.
B. Configure IPS mode when creating or editing a policy rule under the Cisco FMC intrusion tab in Access Policies section by unchecking the “Drop when inline” option.
C. Configure iDS mode when creating or editing a policy rule under the Cisco FMC intrusion tab in Access Policies section by checking the “Drop when inline” option.
D. Configure iDS mode when creating or editing a policy rule under the Cisco FMC intrusion tab in Access Policies section by unchecking the “Drop when inline” option.
Answer: B
Question 127
An engineer is using the configure manager add <FMC IP> Cisc404225383 command to add a new Cisco FTD device to the Cisco FMC; however, the device is not being added. Why is this occurring?
A. DONOTRESOLVE must be added to the command
B. The IP address used should be that of the Cisco FTD, not the Cisco FMC
C. The registration key is missing from the command
D. The NAT ID is required since the Cisco FMC is behind a NAT device
Answer: D
Question 128
An engineer is configuring Cisco FMC and wants to allow multiple physical interfaces to be part of the same VLAN. The managed devices must be able to perform Layer 2 switching between interfaces, including subinterfaces. What must be configured to meet these requirements?
A. inter-chassis clustering VLAN
B. Cisco ISE Security Group Tag
C. interface-based VLAN switching
D. integrated routing and bridging
Answer: D
Question 129
An engineer must investigate a connectivity issue and decides to use the packet capture feature on Cisco FTD. The goal is to see the real packet going through the Cisco FTD device and see Snort detection actions as a part of the output. After the capture-traffic command is issued, only the packets are displayed. Which action resolves this issue?
A. Specify the trace using the -T option after the capture-traffic command
B. Perform the trace within the Cisco FMC GUI instead of the Cisco FMC CLI
C. Use the verbose option as a part of the capture-traffic command
D. Use the capture command and specify the trace option to get the required information
Answer: D
Question 130
An analyst using the security analyst account permissions is trying to view the Correlations Events Widget but is not able to access it. However, other dashboards are accessible. Why is this occurring?
A. The widget is configured to display only when active events are present
B. The security analyst role does not have permission to view this widget
C. An API restriction within the Cisco FMC is preventing the widget from displaying
D. The widget is not configured within the Cisco FMC
Answer: B
Question 131
An analyst is reviewing the Cisco FMC reports for the week. They notice that some peer-to-peer applications are being used on the network and they must identify which poses the greatest risk to the environment. Which report gives the analyst this information?
A. Attacks Risk Report
B. User Risk Report
C. Network Risk Report
D. Advanced Malware Risk Report
Answer: C
Question 132
A Cisco FTD has two physical interfaces assigned to a BVI. Each interface is connected to a different VLAN on the same switch. Which firewall mode is the Cisco FTD set up to support?
A. active/active failover
B. transparent
C. routed
D. high availability clustering
Answer: C
Question 133
An engineer wants to connect a single IP subnet through a Cisco FTD firewall and enforce policy. There is a requirement to present the internal IP subnet to the outside as a different IP address. What must be configured to meet these requirements?
A. Configure the downstream router to perform NAT.
B. Configure the upstream router to perform NAT.
C. Configure the Cisco FTD firewall in routed mode with NAT enabled.
D. Configure the Cisco FTD firewall in transparent mode with NAT enabled.
Answer: C
Question 134
Upon detecting a flagrant threat on an endpoint, which two technologies instruct Cisco identity Services Engine to contain the infected endpoint either manually or automatically? (Choose two)
A. Cisco ASA 5500 Series
B. Cisco FMC
C. Cisco AMP
D. Cisco Stealthwatch
E. Cisco ASR 7200 Series
Answer: BC
Question 135
An engineer must configure a Cisco FMC dashboard in a child domain. Which action must be taken so that the dashboard is visible to the parent domain?
A. Add a separate tab.
B. Adjust policy inheritance settings.
C. Add a separate widget.
D. Create a copy of the dashboard.
Answer: D
Question 136
An engineer runs the command restore remote-manager-backup location 2.2.2.2 admin /Volume/home/admin FTD408566513.zip on a Cisco FMC. After connecting to the repository, the Cisco FTD device is unable to accept the backup file. What is the reason for this failure?
A. The backup file is not in .cfg format.
B. The wrong IP address is used.
C. The backup file extension was changed from .tar to .zip.
D. The directory location is incorrect.
Answer: C
Question 137
An engineer is configuring Cisco FMC and wants to limit the time allowed for processing packets through the interface. However if the time is exceeded the configuration must allow packets to bypass detection. What must be configured on the Cisco FMC to accomplish this task?
A. Fast-Path Rules Bypass
B. Cisco ISE Security Group Tag
C. inspect Local Traffic Bypass
D. Automatic Application Bypass
Answer: D
Question 138
A network engineer sets up a secondary Cisco FMC that is integrated with Cisco Security Packet Analyzer.What occurs when the secondary Cisco FMC synchronizes with the primary Cisco FMC?
A. The existing integration configuration is replicated to the primary Cisco FMC
B. The existing configuration for integration of the secondary Cisco FMC the Cisco Security Packet Analyzer is overwritten.
C. The synchronization between the primary and secondary Cisco FMC fails
D. The secondary Cisco FMC must be reintegrated with the Cisco Security Packet Analyzer after the synchronization
Answer: B
Question 139
A network administrator is deploying a Cisco IPS appliance and needs it to operate initially without affecting traffic flows. it must also collect data to provide a baseline of unwanted traffic before being reconfigured to drop it. Which Cisco IPS mode meets these requirements?
A. failsafe
B. inline tap
C. promiscuous
D. bypass
Answer: C
Question 140
A network administrator is implementing an active/passive high availability Cisco FTD pair. When adding the high availability pair, the administrator cannot select the secondary peer. What is the cause?
A. The second Cisco FTD is not the same model as the primary Cisco FTD.
B. An high availability license must be added to the Cisco FMC before adding the high availability pair.
C. The failover link must be defined on each Cisco FTD before adding the high availability pair.
D. Both Cisco FTD devices are not at the same software version.
Answer: A
Question 141
A company is in the process of deploying intrusion protection with Cisco FTDs managed by a Cisco FMC. Which action must be selected to enable fewer rules detect only critical conditions and avoid false positives?
A. Connectivity Over Security
B. Balanced Security and Connectivity
C. Maximum Detection
D. No Rules Active
Answer: A
Question 142
An engineer is troubleshooting a file that is being blocked by a Cisco FTD device on the network. The user is reporting that the file is not malicious. Which action does the engineer take to identify the file and validate whether or not it is malicious?
A. identify the file in the intrusion events and submit it to Threat Grid for analysis.
B. Use FMC file analysis to look for the file and select Analyze to determine its disposition.
C. Use the context explorer to find the file and download it to the local machine for investigation.
D. Right click the connection event and send the file to AMP for Endpoints to see if the hash is malicious.
Answer: A
Question 143
Which protocol is needed to exchange threat details in rapid threat containment on Cisco FMC?
A. SGT
B. SNMP v3
C. BFD
D. pxGrid
Answer: D



hi, right answer is capture
capture-traffic -> Display traffic or save to specified file
How many questions are in part 3 ?
45 questions in part 3
The right answer should be “block” in this context ? There is high number of malicious files, with “allow” they go for inspection. but block is right in this context I think
https://www.cisco.com/c/en/us/support/docs/security/firepower-management-center/212699-configure-ftd-high-availability-on-firep.html#anc4
In order to create an HA between 2 FTD devices, these conditions must be met:
Same model
Same version (this applies to FXOS and to FTD – (major (first number), minor (second number), and maintenance (third number) must be equal))
Same number of interfaces
Same type of interfaces
Both devices as part of the same group/domain in FMC
Have identical Network Time Protocol (NTP) configuration
Be fully deployed on the FMC without uncommitted changes
Be in the same firewall mode: routed or transparent.
Note that this must be checked on both FTD devices and FMC GUI since there have been cases where the FTDs had the same mode, but FMC does not reflect this.
Does not have DHCP/Point-to-Point Protocol over Ethernet (PPPoE) configured in any of the interfaces
Different hostname (Fully Qualified Domain Name (FQDN)) for both chassis. In order to check the chassis hostname navigate to FTD CLI and run this command:
This is wrong question. its for Cisco Trust Anchor question…
Question 40
Which function is the primary function of Cisco AMP threat Grid?
A. flood attack detection.
B. secure boot
C. image signing
D. DDoS mitigation
E. SYN flood detection
Answer: B C
Taking as reference the steps to Replace a Primary FTD HA Unit from cisco (https://www.cisco.com/c/en/us/td/docs/security/firepower/601/configuration/guide/fpmc-config-guide-v601/fpmc-config-guide-v601_chapter_01100110.pdf) page 21. The right answer is D. Unregister the faulty Cisco FTD device from the Cisco FMC.
Step 1 Choose Force Break to separate the high availability pair; see Separate Units in a High Availability Pair, on
page 22.
The break operation removes all the configuration related to HA from Firepower Threat Defense
and Firepower Management Center, and you need to recreate it manually later. To successfully
configure the same HA pair, ensure that you save the IPs, MAC addresses, and monitoring
configuration of all the interfaces/subinterfaces prior to executing the HA break operation.
Note
Step 2 Unregister the failed primary Firepower Threat Defense device from the Firepower Management Center; see
Deleting Devices from the Firepower Management Center.
Step 3 Register the replacement Firepower Threat Defense to the Firepower Management Center; see Add Devices
to the Firepower Management Center
Hi,
Please share materials you use to study 300-710. Dumps, tutorials, or books. Thanks
The right answer is D ??
Anybody can help to explain why packet capture or packet tracer were used for below questions.
Part 1 – Question 42
A connectivity issue is occurring between a client and a server which are communicating through a Cisco Firepower device While troubleshooting, a network administrator sees that traffic is reaching the server, but the client is not getting a response. Which step must be taken to resolve this issue without initiating traffic from the client?
A. Use packet-tracer to ensure that traffic is not being blocked by an access list.
B. Use packet capture to ensure that traffic is not being blocked by an access list.
C. Use packet capture to validate that the packet passes through the firewall and is NATed to the corrected IP address.
D. Use packet-tracer to validate that the packet passes through the firewall and is NATed to the corrected IP address.
Answer: D
Part 2 – Question 62
An administrator is attempting to remotely log into a switch in the data centre using SSH and is unable to connect. How does the administrator confirm that traffic is reaching the firewall?
A. by running Wireshark on the administrator’s PC
B. by performing a packet capture on the firewall.
C. by running a packet tracer on the firewall.
D. by attempting to access it from a different workstation.
Answer: B
@cftut, Please help to review Part 2 – Question 74
Question 74
What is a characteristic of bridge groups on a Cisco FTD?
A. in routed firewall mode, routing between bridge groups must pass through a routed interface.
B. in routed firewall mode, routing between bridge groups is supported.
C. in transparent firewall mode, routing between bridge groups is supported
D. Routing between bridge groups is achieved only with a router-on-a-stick configuration on a connected router
Answer: B
Correct answer is “A. in routed firewall mode, routing between bridge groups must pass through a routed interface.”
Reference:
https://www.cisco.com/c/en/us/td/docs/security/firepower/640/configuration/guide/fpmc-config-guide-v64/transparent_or_routed_firewall_mode_for_firepower_threat_defense.html
About Bridge Groups
A bridge group is a group of interfaces that the FTD device bridges instead of routes. Bridge groups are supported in both transparent and routed firewall mode.
About Routed Firewall Mode
In routed mode, the FTD device is considered to be a router hop in the network. Each interface that you want to route between is on a different subnet.
With Integrated Routing and Bridging, you can use a “bridge group” where you group together multiple interfaces on a network, and the FTD device uses bridging techniques to pass traffic between the interfaces. Each bridge group includes a Bridge Virtual Interface (BVI) to which you assign an IP address on the network. The FTD device routes between BVIs and regular routed interfaces.
Disregard previous question.
Part 2 – Question 74
Missed the word “routing” for transparent mode. Routing is not supported in transparent mode. Correct answer should still be B, in routed firewall mode, routing between bridge groups is supported.
Did someone pass recently, how was your experience? please share. Thanks.
Hi there, are there simulations in this exam?
total 218 questions on this dump
please share a valid dump konsanyf at yahoo at gr
Q22
In a switched Firepower device deployment, the protocol that typically establishes network redundancy is the Hot Standby Router Protocol (HSRP). Therefore, the correct answer is B. HSRP.
Question 130
An analyst using the security analyst account permissions is trying to view the Correlations Events Widget but is not able to access it. However, other dashboards are accessible. Why is this occurring?
A. The widget is configured to display only when active events are present
B. The security analyst role does not have permission to view this widget (WRONG ANSWER)
C. An API restriction within the Cisco FMC is preventing the widget from displaying
D. The widget is not configured within the Cisco FMC (CORRECT ANSWER)
https://www.cisco.com/c/en/us/td/docs/security/firepower/610/configuration/guide/fpmc-config-guide-v61/dashboards.html
Anybody can help to explain why packet capture or packet tracer were used for below questions.
Part 1 – Question 42
A connectivity issue is occurring between a client and a server which are communicating through a Cisco Firepower device While troubleshooting, a network administrator sees that traffic is reaching the server, but the client is not getting a response. Which step must be taken to resolve this issue without initiating traffic from the client?
A. Use packet-tracer to ensure that traffic is not being blocked by an access list.
B. Use packet capture to ensure that traffic is not being blocked by an access list.
C. Use packet capture to validate that the packet passes through the firewall and is NATed to the corrected IP address.
D. Use packet-tracer to validate that the packet passes through the firewall and is NATed to the corrected IP address.
Answer: D
Key words in this question “without initiating traffic from the server”. In order to use packet capture effectively you would need to initiate traffic from the server. Packet tracer on the other hand you can simulate the necessary traffic by specifying the protocol number in your packet trace command without having to bother the problem server for real traffic.
Part 2 – Question 62
An administrator is attempting to remotely log into a switch in the data centre using SSH and is unable to connect. How does the administrator confirm that traffic is reaching the firewall?
A. by running Wireshark on the administrator’s PC
B. by performing a packet capture on the firewall.
C. by running a packet tracer on the firewall.
D. by attempting to access it from a different workstation.
Answer: B
This question, there is no mention about not be able to initiate the real traffic from the server or wherever, therefore you can certainly use packet tracer HOWEVER the best way of troubleshooting this would be to initate real traffic and use packet capture
@CFTUT
Question 64
The event dashboard within the Cisco FMC has been inundated with low priority intrusion drop events, which are overshadowing high priority events. An engineer has been tasked with reviewing the policies and reducing the low priority events. Which action should be configured to accomplish this task?
A. generate events
B. drop packet
C. drop connection
D. drop and generate
Answer: A
(The below link is broken)
https://www.cisco.com/c/en/us/td/docs/security/firepower/620/configuration/guide/fpmc-config- guide-v62/
working_with_intrusion_events.html
The correct answer according to the below is : B
Please doublecheck. Thanks.
@Jay: Thank you for your information, we updated it!
IT management is asking the network engineer to provide high-level summary statistics of the Cisco FTD appliance in the network. The business is approaching a peak season so the need to maintain business uptime is high. Which report type should be used to gather this information?
A. Malware Report
B. Standard Report
C. SNMP Report
D. Risk Report
i am with standard report
tandard Report would be the best option to gather high-level summary statistics of the Cisco FTD appliance in the network. Standard Reports provide summary-level data for different aspects of network security such as threats, applications, web usage, network discovery, and more. They offer a quick way to get an overview of the network’s security posture and can be customized to focus on specific aspects of interest to IT management. SNMP Reports, on the other hand, are used to monitor network performance and availability, while Malware Reports and Risk Reports focus on specific aspects of network security.
Dear team,
can you please share any valid and updated dumps?
I used q311 from preway and failed the exam today.
Hi CFTUT,
Question 74
What is a characteristic of bridge groups on a Cisco FTD?
Better answer should be: in routed firewall mode, routing between bridge groups is supported.
– Verson 7.0 says: Bridge groups are supported in both transparent and routed firewall mode.
https://www.cisco.com/c/en/us/td/docs/security/firepower/70/configuration/guide/fpmc-config-guide-v70/transparent_or_routed_firewall_mode_for_firepower_threat_defense.html?bookSearch=true#id_37129:~:text=Bridge%20groups%20are%20supported%20in%20both%20transparent%20and%20routed%20firewall%20mode.
@Anonymous: Thank you for your information. So this question has two correct answers. This question is rather old so not sure which version of FTD they want to ask.
should be D. Create a file policy and set the access control policy to block !!!!
Question 69
An organization has noticed that malware was downloaded from a website that does not currently have a known bad reputation. How will this issue be addresses globally in the quickest way possible and with the least amount of impact?
A. by denying outbound web access
B. Cisco Talos will automatically update the policies.
C. by isolating the endpoint
D. by creating a URL object in the policy to block the website
Why D? least amount of impact then should be B.