SNCF Questions – Part 1
Question 1
What is the role of the casebook feature in Cisco Threat Response?
A. sharing threat analysts
B. pulling data via the browser extension
C. triage automaton with alerting
D. alert prioritization
Answer: A
Explanation
Casebook – It is used to record, organize, and share sets of observables of interest primarily during an investigation and threat analysis. You can use a casebook to get the current verdicts or dispositions on the observables.
Question 2
An administrator is adding a new URL-based category feed to the Cisco FMC for use within the policies. The intelligence source does not use STIX. but instead uses a .txt file format. Which action ensures that regular updates are provided?
A. Add a URL source and select the flat file type within Cisco FMC.
B. Upload the .txt file and configure automatic updates using the embedded URL.
C. Add a TAXII feed source and input the URL for the feed.
D. Convert the .txt file to STIX and upload it to the Cisco FMC.
Answer: A
Question 3
An engineer installs a Cisco FTD device and wants to inspect traffic within the same subnet passing through a firewall and inspect traffic destined to the Internet. Which configuration will meet this requirement?
A. transparent firewall mode with IRB only
B. routed firewall mode with BVI and routed interfaces
C. transparent firewall mode with multiple BVIs
D. routed firewall mode with routed interfaces only
Answer: B
Question 4
A network administrator configured a NAT policy that translates a public IP address to an internal web server IP address. An access policy has also been created that allows any source to reach the public IP address on port 80. The web server is still not reachable from the Internet on port 80. Which configuration change is needed?
A. The intrusion policy must be disabled for port 80.
B. The access policy rule must be configured for the action trust.
C. The NAT policy must be modified to translate the source IP address as well as destination IP address.
D. The access policy must allow traffic to the internal web server IP address.
Answer: D
Question 5
A network administrator is migrating from a Cisco ASA to a Cisco FTD. EIGRP is configured on the Cisco ASA but it is not available in the Cisco FMC. Which action must the administrator take to enable this feature on the Cisco FTD?
A. Configure EIGRP parameters using FlexConfig objects.
B. Add the command feature-eigrp via the FTD CLI.
C. Create a custom variable set and enable the feature in the variable set.
D. Enable advanced configuration options in the FMC.
Answer: A
Explanation
EIGRP is not natively supported by FTD so we need to use FlexConfig to push EIGRP commands to FTD.
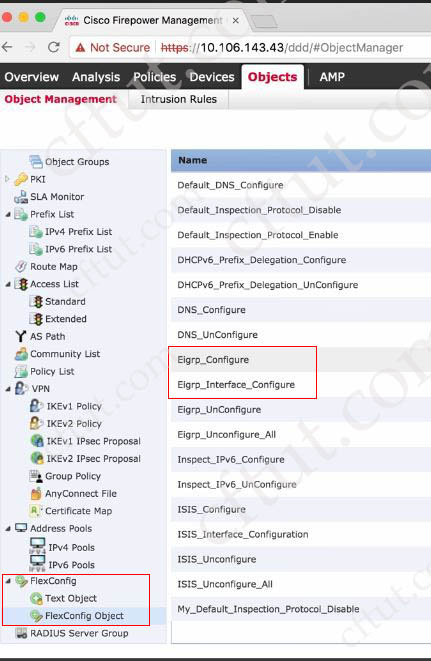
Question 6
A security engineer found a suspicious file from an employee email address and is trying to upload it for analysis, however the upload is failing. The last registration status is still active. What is the cause for this issue?
A. Cisco AMP for Networks is unable to contact Cisco Threat Grid on premise.
B. Cisco AMP for Networks is unable to contact Cisco Threat Grid Cloud.
C. There is a host limit set.
D. The user agent status is set to monitor.
Answer: C
Question 7
An administrator is attempting to add a new FTD device to their FMC behind a NAT device with a NAT ID of NAT001 and a password of Cisco0420l06525. The private IP address of the FMC server is 192.168.45.45 which is being translated to the public IP address of 209.165.200.225/27. Which command set must be used in order to accomplish this task?
A. configure manager add 209.165.200.225 <reg_key> <nat_id>
B. configure manager add 192.168.45.45 <reg_key> <nat_id>
C. configure manager add 209.165.200.225 255.255.255.224 <reg_key> <nat_id>
D. configure manager add 209.165.200.225/27 <reg_key> <nat_id>
Answer: A
Question 8
A security analyst must create a new report within Cisco FMC to show an overview of the daily attacks, vulnerabilities, and connections. The analyst wants to reuse specific dashboards from other reports to create this consolidated one. Which action accomplishes this task?
A. Create a dashboard object via Object Management to represent the desired views.
B. Modify the Custom Workflows within the Cisco FMC to feed the desired data into the report.
C. Copy the Malware Report and modify the sections to pull components from other reports.
D. Use the import feature in the newly created report to select which dashboards to add.
Answer: D
Question 9
A network engineer must provide redundancy between two Cisco FTD devices. The redundancy configuration must include automatic configuration, translation, and connection updates. After the initial configuration of the two appliances, which two steps must be taken to proceed with the redundancy configuration? (Choose two)
A. Configure the virtual MAC address on the failover link.
B. Disable hellos on the inside interface.
C. Configure the standby IP addresses.
D. Ensure the high availability license is enabled.
E. Configure the failover link with stateful properties.
Answer: C E
Explanation
Configure FTD High Availability on Firepower Appliances
…
Step 4. Configure the Data interfaces (primary and standby IP addresses)
Step 10. Stay on the High Availability tab and configure Virtual MAC addresses
We don’t configure the virtual MAC on the failover link but on the link to the network -> Answer A is not correct.
Question 10
An engineer attempts to pull the configuration for a Cisco FTD sensor to review with Cisco TAC but does not have direct access to the CLI for the device. The CLI for the device is managed by Cisco FMC to which the engineer has access. Which action in Cisco FMC grants access to the CLI for the device?
A. Export the configuration using the Import/Export tool within Cisco FMC.
B. Create a backup of the configuration within the Cisco FMC.
C. Use the show run all command in the Cisco FTD CLI feature within Cisco FMC.
D. Download the configuration file within the File Download section of Cisco FMC.
Answer: C
Question 11
Which policy rule is included in the deployment of a local DMZ during the initial deployment of a Cisco NGFW through the Cisco FMC GUI?
A. a default DMZ policy for which only a user can change the IP addresses.
B. deny ip any
C. no policy rule is included
D. permit ip any
Answer: C
Question 12
Which limitation applies to Cisco FMC dashboards in a multidomain environment?
A. Child domains can view but not edit dashboards that originate from an ancestor domain.
B. Child domains have access to only a limited set of widgets from ancestor domains.
C. Only the administrator of the top ancestor domain can view dashboards.
D. Child domains cannot view dashboards that originate from an ancestor domain.
Answer: D
Explanation
In a multidomain deployment, you cannot view dashboards from ancestor domains; however, you can create new dashboards that are copies of the higher-level dashboards.
Question 13
Which command is run on an FTD unit to associate the unit to an FMC manager that is at IP address 10.0.0.10, and that has the registration key Cisco123?
A. configure manager local 10.0.0.10 Cisco123
B. configure manager add Cisco123 10.0.0.10
C. configure manager local Cisco123 10.0.0.10
D. configure manager add 10.0.0.10 Cisco123
Answer: D
Question 14
Which Cisco Firepower feature is used to reduce the number of events received in a period of time?
A. rate-limiting
B. suspending
C. correlation
D. thresholding
Answer: D
Question 15
While integrating Cisco Umbrella with Cisco Threat Response, a network security engineer wants to automatically push blocking of domains from the Cisco Threat Response interface to Cisco Umbrella. WhichAPI meets this requirement?
A. investigate
B. reporting
C. enforcement
D. REST
Answer: C
Question 16
The CIO asks a network administrator to present to management a dashboard that shows custom analysis tables for the top DNS queries URL category statistics, and the URL reputation statistics. Which action must the administrator take to quickly produce this information for management?
A. Run the Attack report and filter on DNS to show this information.
B. Create a new dashboard and add three custom analysis widgets that specify the tables needed.
C. Modify the Connection Events dashboard to display the information in a view for management.
D. Copy the intrusion events dashboard tab and modify each widget to show the correct charts.
Answer: B
Question 17
An analyst is investigating a potentially compromised endpoint within the network and pulls a host report for the endpoint in Qto collect metrics and documentation. What information should be taken from this report for the investigation?
A. client applications by user, web applications, and user connections
B. number of attacked machines, sources of the attack, and traffic patterns
C. threat detections over time and application protocols transferring malware
D. intrusion events, host connections, and user sessions
Answer: D
Question 18
A network administrator reviews the file report for the last month and notices that all file types, except exe show a disposition of unknown. What is the cause of this issue?
A. The malware license has not been applied to the Cisco FTD.
B. The Cisco FMC cannot reach the Internet to analyze files.
C. A file policy has not been applied to the access policy.
D. Only Spero file analysis is enabled.
Answer: D
Question 19
An administrator receives reports that users cannot access a cloud-hosted web server. The access control policy was recently updated with several new policy additions and URL filtering. What must be done to troubleshoot the issue and restore access without sacrificing the organization’s security posture?
A. Create a new access control policy rule to allow ports 80 and 443 to the FQDN of the web server.
B. Identify the blocked traffic in the Cisco FMC connection events to validate the block, and modify the policy to allow the traffic to the web server.
C. Verify the blocks using the packet capture tool and create a rule with the action monitor for the traffic.
D. Download a PCAP of the traffic attempts to verify the blocks and use the flexconfig objects to create a rule that allows only the required traffic to the destination server.
Answer: B
Question 20
A network security engineer must export packet captures from the Cisco FMC web browser while troubleshooting an issue. When navigating to the address https://<FMC IP>/capture/CAPI/pcap/test.pcap, an error 403: Forbidden is given instead of the PCAP file. Which action must the engineer take to resolve this issue?
A. Disable the proxy setting on the browser
B. Disable the HTTPS server and use HTTP instead
C. Use the Cisco FTD IP address as the proxy server setting on the browser
D. Enable the HTTPS server for the device platform policy
Answer: D
Question 21
An engineer wants to change an existing transparent Cisco FTD to routed mode. The device controls traffic between two network segments. Which action is mandatory to allow hosts to reestablish communication between these two segments after the change?
A. Remove the existing dynamic routing protocol settings.
B. Configure multiple BVIs to route between segments.
C. Assign unique VLAN IDs to each firewall interface.
D. Implement non-overlapping IP subnets on each segment.
Answer: D
Question 22
An engineer is reviewing a ticket that requests to allow traffic for some devices that must connect to a server over 8699/udp. The request mentions only one IP address, 172.16.18.15, but the requestor asked for the engineer to open the port for all machines that have been trying to connect to it over the last week. Which action must the engineer take to troubleshoot this issue?
A. Use the context explorer to see the application blocks by protocol.
B. Use the context explorer to see the destination port blocks
C. Filter the connection events by the source port 8699/udp.
D. Filter the connection events by the destination port 8699/udp.
Answer: D
Question 23
An organization is migrating their Cisco ASA devices running in multicontext mode to Cisco FTD devices. Which action must be taken to ensure that each context on the Cisco ASA is logically separated in the Cisco FTD devices?
A. Add a native instance to distribute traffic to each Cisco FTD context.
B. Add the Cisco FTD device to the Cisco ASA port channels.
C. Configure a container instance in the Cisco FTD for each context in the Cisco ASA.
D. Configure the Cisco FTD to use port channels spanning multiple networks.
Answer: C
Question 24
A security engineer is configuring a remote Cisco FTD that has limited resources and internet bandwidth. Which malware action and protection option should be configured to reduce the requirement for cloud lookups?
A. Malware Cloud Lookup and dynamic analysis
B. Block Malware action and dynamic analysis
C. Block Malware action and local malware analysis
D. Block File action and local malware analysis
Answer: C
Question 25
Refer to the exhibit.
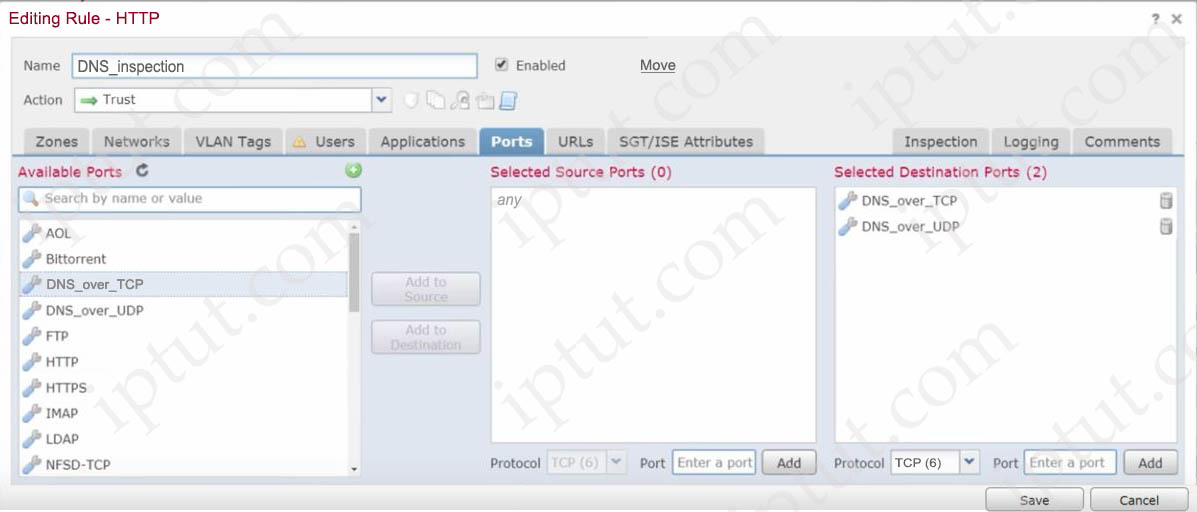
Engineer is modifying an access control pokey to add a rule to inspect all DNS traffic that passes through the firewall. After making the change and deploying the policy they see that DNS traffic is not being inspected by the Snort engine. What is the problem?
A. The rule must specify the security zone that originates the traffic
B. The rule must define the source network for inspection as well as the port
C. The action of the rule is set to trust instead of allow.
D. The rule is configured with the wrong setting for the source port
Answer: C
Question 27
A network administrator has converted a Cisco FTD from using LDAP to LDAPS for VPN authentication. The Cisco FMC can connect to the LDAPS server, but the Cisco FTD is not connecting, Which configuration must be enable on the Cisco FTD?
A. SSL must be set to a use TLSv1.2 or lower
B. DNS servers must be defined for name resolution
C. The RADIUS server must be defined
D. The LDAPS must be allowed through the access policy
Answer: B
Question 28
A security engineer must deploy a Cisco FTD appliance as a bump in the wire to detect intrusion events without disrupting the flow of network traffic. Which two features must be configured to accomplish the task? (Choose two.)
A. inline set pair
B. transparent mode
C. tap mode
D. passive interfaces
E. bridged mode
Answer: A C
Question 29
A network administrator is configuring an FTD in transparent mode. A bridge group is set up and an access policy has been set up t o allow all IP traffic. Traffic is not passing through the FTD. What additional configuration is needed?
A. The security levels of the interfaces must be set.
B. A default route must be added to the FTD.
C. An IP address must be assigned to the BVI.
D. A mac-access control list must be added to allow all MAC addresses.
Answer: C
Question 30
What is the difference between inline and inline tap on Cisco Firepower?
A. Inline tap mode can send a copy of the traffic to another device.
B. Inline tap mode does full packet capture.
C. Inline mode cannot do SSL decryption.
D. Inline mode can drop malicious traffic.
Answer: D
Question 31
What are the minimum requirements to deploy a managed device inline?
A. inline interfaces, security zones, MTU, and mode
B. passive interface, MTU, and mode
C. inline interfaces, MTU, and mode
D. passive interface, security zone, MTU, and mode
Answer: C
Question 32
What are two application layer preprocessors? (Choose two.)
A. CIFS
B. IMAP
C. SSL
D. DNP3
E. ICMP
Answer: B C
Question 33
With Cisco Firepower Threat Defense software, which interface mode must be configured to passively receive traffic that passes through the appliance?
A. inline set
B. passive
C. routed
D. inline tap
Answer: D
Explanation
In passive mode, the copy of the traffic will be sent to FTD from a network device for traffic inspection, and original traffic never passes through it. ‘Inline TAP’ also copies the traffic passing through the appliance, but no action is taken.
Question 34
Which two statements about bridge-group interfaces in Cisco FTD are true? (Choose two.)
A. The BVI IP address must be in a separate subnet from the connected network.
B. Bridge groups are supported in both transparent and routed firewall modes.
C. Bridge groups are supported only in transparent firewall mode.
D. Bidirectional Forwarding Detection echo packets are allowed through the FTD when using bridge- group members.
E. Each directly connected network must be on the same subnet.
Answer: B E
Explanation
“A bridge group is a group of interfaces that the FTD device bridges instead of routes. Bridge groups are supported in both transparent and routed firewall mode.”
-> Answer B is correct.
Bridge Group Guidelines (TransparentMode)
• You can create up to 250 bridge groups,with 4 interfaces per bridge group.
• Each directly-connected network must be on the same subnet. -> Answer E is correct.
…
Question 35
An engineer wants to add an additional Cisco FTD Version 6.2.3 device to their current 6.2.3 deployment to create a high availability pair. The currently deployed Cisco FTD device is using local management and identical hardware including the available port density to enable the failover and stateful links required in a proper high availability deployment. Which action ensures that the environment is ready to pair the new Cisco FTD with the old one?
A. Change from Cisco FDM management to Cisco FMC management on both devices and register them to FMC.
B. Ensure that the two devices are assigned IP addresses from the 169 254.0.0/16 range for failover interfaces.
C. Factory reset the current Cisco FTD so that it can synchronize configurations with the new Cisco FTD device.
D. Ensure that the configured DNS servers match on the two devices for name resolution.
Answer: A
Question 36
An administrator must use Cisco FMC to install a backup route within the Cisco FTD to route traffic in case of a routing failure with primary route. Which action accomplish this task?
A. Install the static backup route and modify the metric to be less than the primary route
B. Use a default route in the FMC instead of having multiple routes contending for priority
C. Configure EIGRP routing on the FMC to ensure that dynamic routes are always updated
D. Create the backup route and use route tracking on both routes to a destination IP address in the network
Answer: D
Question 37
An administrator is setting up a Cisco FMC and must provide expert mode access for a security engineer. The engineer is permitted to use only a secured out-of-band network workstation with a static IP address to access the Cisco FMC. What must be configured to enable this access?
A. Enable HTTP and define an access list
B. Enable HTTPS and SNMP under the Access List section
C. Enable SCP under the Access List section
D. Enable SSH and define an Access List
Answer: D
Explanation
From FMC version 6.3, we can Enable CLI Access on the System > Configuration > Console Configuration page.
• Checked: Logging into the FMC using SSH accesses the CLI.
• Unchecked: Logging into FMC using SSH accesses the Linux shell. This is the default state
for fresh Version 6.3 installations as well as upgrades to Version 6.3 from a previous release.
To enter expert mode, use the expert command in the CLI to access the Linux shell. Users with Linux shell access can obtain root privileges, which can present a security risk. Therefore we should define an access-list to limit who can access the expert mode.
Question 38
What is the RTC workflow when the infected endpoint is identified?
A. Cisco ISE instructs Cisco AMP to contain the infected endpoint.
B. Cisco ISE instructs Cisco FMC to contain the infected endpoint.
C. Cisco AMP instructs Cisco FMC to contain the infected endpoint.
D. Cisco FMC instructs Cisco ISE to contain the infected endpoint.
Answer: D
Question 39
Due to an increase in malicious events, a security engineer must generate a threat report to include intrusion events, malware events, and security intelligence events. How is this information collected in a single report?
A. Run the default Firepower report.
B. Export the Attacks Risk report.
C. Generate a malware report.
D. Create a Custom report.
Answer: D
Question 40
Which interface type allows packets to be dropped?
A. passive
B. inline
C. ERSPAN
D. TAP
Answer: B
Question 41
An organization does not want to use the default Cisco Firepower block page when blocking HTTP traffic. The organization wants to include information about its policies and procedures to help educate the users whenever a block occurs. Which two steps must be taken to meet these requirements? (Choose two.)
A. Edit the HTTP request handling in the access control policy to customized block
B. Modify the system-provided block page result using Python
C. Create HTML code with the information for the policies and procedures
D. Change the HTTP response in the access control policy to custom
E. Write CSS code with the information for the policies and procedures
Answer: C D
Question 42
A connectivity issue is occurring between a client and a server which are communicating through a Cisco Firepower device While troubleshooting, a network administrator sees that traffic is reaching the server, but the client is not getting a response. Which step must be taken to resolve this issue without initiating traffic from the client?
A. Use packet-tracer to ensure that traffic is not being blocked by an access list.
B. Use packet capture to ensure that traffic is not being blocked by an access list.
C. Use packet capture to validate that the packet passes through the firewall and is NATed to the corrected IP address.
D. Use packet-tracer to validate that the packet passes through the firewall and is NATed to the corrected IP address.
Answer: D
Question 43
A company has many Cisco FTD devices managed by a Cisco FMC. The security model requires that access control rule logs be collected for analysis. The security engineer is concerned that the Cisco FMC will not be able to process the volume of logging that will be generated. Which configuration addresses concern this?
A. Send Cisco FTD connection events directly to a SIEM system and forward security events from Cisco FMC to the SIEM system for storage and analysis
B. Send Cisco FTD connection events and security events directly to SIEM system for storage and analysis
C. Send Cisco FTD connection events and security events to a cluster of Cisco FMC devices for storage and analysis
D. Send Cisco FTD connection events and security events to Cisco FMC and configure it to forward logs to SIEM for storage and analysis
Answer: A
Explanation
Since FTD 6.3 syslogs can be sent from FTD directly.

Therefore the best solution is sending connection & intrusion events directly to SIEM and forwarding security events from FMC to SIEM.
Reference: https://panenka.sk/cisco-fmc-ftd-eventing/
Question 44
An engineer is setting up a new Firepower deployment and is looking at the default FMC policies to start the implementation. During the initial trial phase, the organization wants to test some common Snort rules while still allowing the majority of network traffic to pass. Which default policy should be used?
A. Maximum Detection
B. Security Over Connectivity
C. Balanced Security and Connectivity
D. Connectivity Over Security
Answer: D
Question 45
An engineer integrates Cisco FMC and Cisco ISE using pxGrid. Which role is assigned for Cisco FMC?
A. server
B. controller
C. publisher
D. client
Answer: C
Explanation
pxGrid stands for Platform Exchange Grid, and it is a technology that allows integrating multiple vendors security products together and grouping them in an ecosystem domain. The main purpose of using pxGrid is to share contextual data between the integrated partners.
pxGrid uses a built-in API in ISE and it is comprised of three main components which are the controller, publisher and the subscriber. The controller is the core component to make everything working and as said is going to be ISE. The publisher instead is the partner that has some contextual data to be shared with the other partners. And finally the subscriber is the partner that is interested in parsing some contextual data from the other partners.
Reference: https://bluenetsec.com/fmc-pxgrid-integration-with-ise/
Therefore the controller is ISE, there is no “subscriber” option so the best answer should be “publisher”.
Question 46
A network administrator notices that remote access VPN users are not reachable from inside the network. It is determined that routing is configured correctly, however return traffic is entering the firewall but not leaving it. What is the reason for this issue?
A. A manual NAT exemption rule does not exist at the top of the NAT table.
B. An external NAT IP address is not configured.
C. An external NAT IP address is configured to match the wrong interface.
D. An object NAT exemption rule does not exist at the top of the NAT table.
Answer: A
Question 47
An engineer is troubleshooting connectivity to the DNS servers from hosts behind a new Cisco FTD device. The hosts cannot send DNS queries to servers in the DMZ. Which action should the engineer take to troubleshoot this issue using the real DNS packets?
A. Use the packet capture tool to check where the traffic is being blocked and adjust the access control or intrusion policy as needed
B. Use the Connection Events dashboard to check the block reason and adjust the inspection policy as needed
C. Use the packet tracer tool to determine at which hop the packet is being dropped
D. Use the show blocks command in the Threat Defense CLI tool and create a policy to allow the blocked traffic
Answer: B
Explanation
It seems a DNS policy has blocked the DNS queries so we should check the “Connection Events” dashboard first to find out the issue.
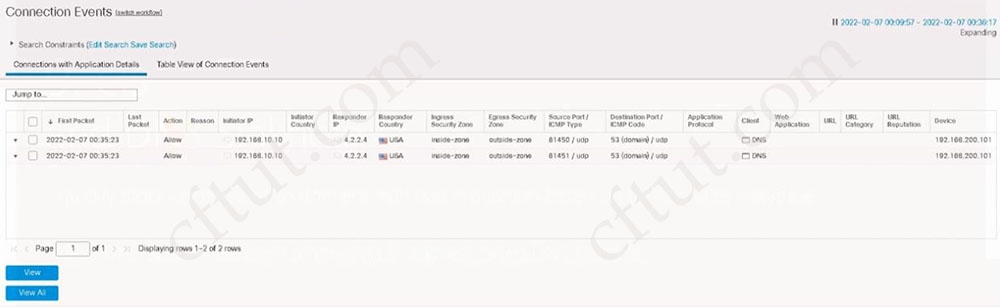
Question 48
A network engineer implements a new Cisco Firepower device on the network to take advantage of its intrusion detection functionality. There is a requirement to analyze the traffic going across the device, alert on any malicious traffic, and appear as a bump in the wire How should this be implemented?
A. Specify the BVl IP address as the default gateway for connected devices.
B. Enable routing on the Cisco Firepower
C. Add an IP address to the physical Cisco Firepower interfaces.
D. Configure a bridge group in transparent mode.
Answer: D
Question 49
Which Cisco FMC report gives the analyst information about the ports and protocols that are related to the configured sensitive network for analysis?
A. Malware Report
B. Host Report
C. Firepower Report
D. Network Report
Answer: A
Question 50
A security engineer must configure a Cisco FTD appliance to inspect traffic coming from the internet. The Internet traffic will be mirrored from the Cisco Catalyst 9300 Switch. Which configuration accomplishes the task?
A. Set interface configuration mode to none.
B. Set the firewall mode to transparent.
C. Set the firewall mode to routed.
D. Set interface configuration mode to passive.
Answer: D
Question 51
A network administrator registered a FTD to an existing FMC. The administrator cannot place the FTD in transparent mode. Which action enables transparent mode?
A. Add a Bridge Group Interface to the FTD before transparent mode is configured.
B. Deregister the FTD device from FMC and configure transparent mode via the CLI.
C. Obtain an FTD model that supports transparent mode.
D. Assign an IP address to two physical interfaces.
Answer: B
Question 52
An engineer must add DNS-specific rules to the Cisco FTD intrusion policy. The engineer wants to use the rules currently in the Cisco FTD Snort database that are not already enable but does not want to enable more than are needed.Which action meets these requirements?
A. Change the base policy to Security over Connectivity
B. Change the dynamic state of the rule within the policy
C. Change the rules using the Generate and use recommendations feature
D. Change the rule state within the policy being used
Answer: C
Question 53
A network administrator is trying to convert from LDAP to LDAPS for VPN user authentication on a Cisco FTD. Which action must be taken on the Cisco FTD objects to accomplish this task?
A. Identify the LDAPS cipher suite and use a cipher suite list object to define the Cisco FTD connection requirements
B. Add a key chain object to acquire the LDAP certificate
C. Create a certificate enrollment object to get the LDAPS certificate needed
D. Modify the policy list object to define the session requirements LDAPS
Answer: C
Question 54
A security engineer is deploying a pair of primary and secondary Cisco FMC devices. The secondary must also receive updates from Cisco Talos. Which action achieves this goal?
A. Force failover for the secondary Cisco FMC to synchronize the rule updates from the primary.
B. Configure the secondary Cisco FMC so that it receives updates from Cisco Talos.
C. Manually import rule updates onto the secondary Cisco FMC device.
D. Configure the primary Cisco FMC so that the rules are updated.
Answer: D
Explanation
If your deployment includes a high availability pair of Firepower Management Centers, import the update on the primary only. The secondary Firepower Management Center receives the rule update as part of the regular synchronization process.
Question 55
Which two statements about deleting and re-adding a device to Cisco FMC are true? (Choose two.)
A. An option to re-apply NAT and VPN policies during registration is available, so users do not need to re-apply the policies after registration is completed.
B. Before re-adding the device in Cisco FMC, you must add the manager back in the device.
C. No option to delete and re-add a device is available in the Cisco FMC web interface.
D. The Cisco FMC web interface prompts users to re-apply access control policies.
E. No option to re-apply NAT and VPN policies during registration is available, so users need to re- apply the policies after registration is completed.
Answer: D E
Question 56
What is the maximum bit size that Cisco FMC supports for HTTPS certificates?
A. 1024
B. 8192
C. 4096
D. 2048
Answer: C
Question 57
An engineer is investigating connectivity problems on Cisco Firepower for a specific SGT. Which command allows the engineer to capture real packets that pass through the firewall using an SGT of 64?
A. capture CAP type inline-tag 64 match ip any any
B. capture CAP match 64 type inline-tag ip any any
C. capture CAP headers-only type inline-tag 64 match ip any any
D. capture CAP buffer 64 match ip any any
Answer: A
Question 58
An organization recently implemented a transparent Cisco FTD in their network. They must ensure that the device does not respond to insecure SSL/TLS protocols. Which action accomplishes this task?
A. Modify the device’s settings using the device management feature within Cisco FMC to force only secure protocols.
B. Use the Cisco FTD platform policy to change the minimum SSL version on the device to TLS 1.2.
C. Enable the UCAPL/CC compliance on the device to support only the most secure protocols available.
D. Configure a FlexConfig object to disable any insecure TLS protocols on the Cisco FTD device.
Answer: B
Question 59
Refer to the exhibit.
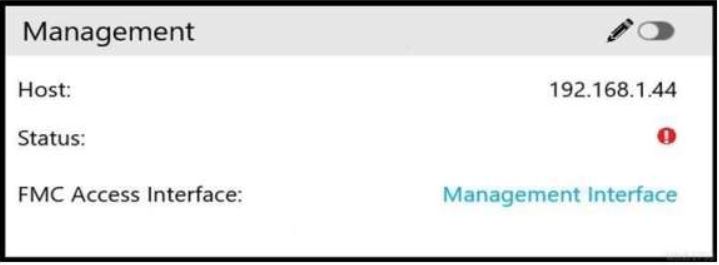
Is the effect of the existing Cisco FMC configuration?
A. The remote management port for communication between the Cisco FMC and the managed device changes to port 8443.
B. The managed device is deleted from the Cisco FMC.
C. The SSL-encrypted communication channel between the Cisco FMC and the managed device becomes plain-text communication channel.
D. The management connection between the Cisco FMC and the Cisco FTD is disabled.
Answer: D
Question 60
An engineer is working on a LAN switch and has noticed that its network connection to the mime Cisco IPS has gone down. Upon troubleshooting it is determined that the switch is working as expected. What must have been implemented for this failure to occur?
A. The upstream router has a misconfigured routing protocol
B. Link-state propagation is enabled
C. The Cisco IPS has been configured to be in fail-open mode
D. The Cisco IPS is configured in detection mode
Answer: B
Question 61
An engineer must define a URL object on Cisco FMC. What is the correct method to specify the URL without performing SSL inspection?
A. Use Subject Common Name value.
B. Specify all subdomains in the object group.
C. Specify the protocol in the object.
D. Include all URLs from CRL Distribution Points.
Answer: A
Question 62
An administrator is creating interface objects to better segment their network but is having trouble adding interfaces to the objects. What is the reason for this failure?
A. The interfaces are being used for NAT for multiple networks.
B. The administrator is adding interfaces of multiple types.
C. The administrator is adding an interface that is in multiple zones.
D. The interfaces belong to multiple interface groups.
Answer: B
Question 63
What is an advantage of adding multiple inline interface pairs to the same inline interface set when deploying an asynchronous routing configuration?
A. Allows the IPS to identify inbound and outbound traffic as part of the same traffic flow.
B. The interfaces disable autonegotiation and interface speed is hard coded set to 1000 Mbps.
C. Allows traffic inspection to continue without interruption during the Snort process restart.
D. The interfaces are automatically configured as a media-independent interface crossover.
Answer: A
Question 64
Which firewall design allows a firewall to forward traffic at layer 2 and layer 3 for the same subnet?
A. Cisco Firepower Threat Defense mode
B. transparent mode
C. routed mode
D. integrated routing and bridging
Answer: D
Question 65
Which feature is supported by IRB on Cisco FTD devices?
A. redundant interface
B. dynamic routing protocol
C. EtherChannel interface
D. high-availability cluster
Answer: A
Question 66
A network administrator is configuring a Cisco AMP public cloud instance and wants to capture infections and polymorphic variants of a threat to help detect families of malware. Which detection engine meets this requirement?
A. RBAC
B. Tetra
C. Ethos
D. Spero
Answer: C
Question 67
Which Cisco AMP for Endpoints policy is used only for monitoring endpoint actively?
A. Windows domain controller
B. audit
C. triage
D. protection
Answer: B
Question 68
Which two actions can be used in an access control policy rule? (Choose two.)
A. Block with Reset
B. Monitor
C. Analyze
D. Discover
E. Block ALL
Answer: A B
Question 69
An organization has a Cisco FTD that uses bridge groups to pass traffic from the inside interfaces to the outside interfaces. They are unable to gather information about neighbouring Cisco devices or use multicast in their environment. What must be done to resolve this issue?
A. Create a firewall rule to allow CDP traffic.
B. Create a bridge group with the firewall interfaces.
C. Change the firewall mode to transparent.
D. Change the firewall mode to routed.
Answer: C
Explanation
Bridge Groups in Routed Firewall Mode
…
In routed firewall mode, broadcast and multicast traffic is blocked even if you allow it in an access rule, including unsupported dynamic routing protocols and DHCP (unless you configure DHCP relay). Within a bridge group, you can allow this traffic with an access rule (using an extended ACL) -> Answer D is not correct.
According to the question, we learn that this organization used bridge groups already -> Answer B is not correct.
Answer A seems to be not correct as the firewall rule only allows CDP traffic, not multicast traffic. So only answer C is left.
Note: Bridge groups are supported in both transparent and routed firewall mode.
Question 70
A network administrator cannot select the link to be used for failover when configuring an active/passive HA Cisco FTD pair. Which configuration must be changed before setting up the high availability pair?
A. An IP address in the same subnet must be added to each Cisco FTD on the interface.
B. The interface name must be removed from the interface on each Cisco FTD.
C. The name Failover must be configured manually on the interface on each Cisco FTD.
D. The interface must be configured as part of a LACP Active/Active EtherChannel.
Answer: B
Question 71
A company wants a solution to aggregate the capacity of two Cisco FTD devices to make the best use of resources such as bandwidth and connections per second. Which order of steps must be taken across theCisco FTDs with Cisco FMC to meet this requirement?
A. Add members to the Cisco FMC, configure Cisco FTD interfaces, create the cluster in Cisco FMC, and configure cluster members in Cisco FMC
B. Add members to Cisco FMC, configure Cisco FTD interfaces in Cisco FMC, configure cluster members in Cisco FMC, create cluster in Cisco FMC, and configure cluster members in Cisco FMC
C. Configure the Cisco FTD interfaces, add members to FMC, configure cluster members in FMC, and create cluster in Cisco FMC
D. Configure the Cisco FTD interfaces and cluster members, add members to Cisco FMC, and create the cluster in Cisco FMC
Answer: D
Question 72
An administrator is configuring their transparent Cisco FTD device to receive ERSPAN traffic from multiple switches on a passive port, but the Cisco FTD is not processing the traffic. What is the problem?
A. The switches do not have Layer 3 connectivity to the FTD device for GRE traffic transmission.
B. The switches were not set up with a monitor session ID that matches the flow ID defined on the Cisco FTD.
C. The Cisco FTD must be in routed mode to process ERSPAN traffic.
D. The Cisco FTD must be configured with an ERSPAN port not a passive port.
Answer: C
Question 73
The administrator notices that there is malware present with an .exe extension and needs to verify if any of the systems on the network are running the executable file. What must be configured within Cisco AMP for Endpoints to show this data?
A. vulnerable software
B. file analysis
C. threat root cause
D. prevalence
Answer: D
Question 74
Refer the exhibit.
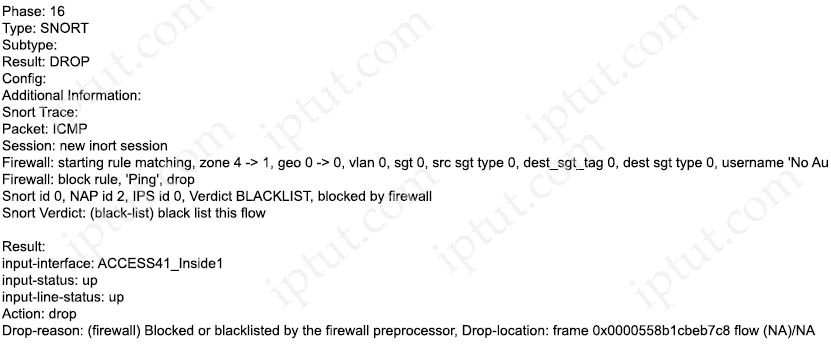
A systems administrator conducts a connectivity test to their SCCM server from a host machine and gets no response from the server. Which action ensures that the ping packets reach the destination and that the host receives replies?
A. Modify the Snort rules to allow ICMP traffic
B. Create an access control policy rule that allows ICMP traffic
C. Configure a custom Snort signature to allow ICMP traffic after inspection
D. Create an ICMP allow list and add the ICMP destination to remove it from the implicit deny list
Answer: D
Question 75
The network administrator wants to enhance the network security posture by enabling machine learning tor malware detection due to a concern with suspicious Microsoft executable file types that were seen while creating monthly security reports for the CIO. Which feature must be enabled to accomplish this goal?
A. Spero
B. dynamic analysis
C. static analysis
D. Ethos
Answer: A



Hi all, are the premium questions up to date?
Question 2 in this list is wrong. There is nowhere to choose a “flat file” format. Instead configure the URL and choose “List”. I tried this on a live instance of FMC.
@CFTUT
Question 54
A security engineer is deploying a pair of primary and secondary Cisco FMC devices. The secondary must also receive updates from Cisco Talos. Which action achieves this goal?
A. Force failover for the secondary Cisco FMC to synchronize the rule updates from the primary.
B. Configure the secondary Cisco FMC so that it receives updates from Cisco Talos.
C. Manually import rule updates onto the secondary Cisco FMC device.
D. Configure the primary Cisco FMC so that the rules are updated.
Answer: B -Wrong answer
The Correct answer is – D
>>If your deployment includes a high availability pair of Firepower Management Centers, import the update on the primary only. The secondary Firepower Management Center receives the rule update as part of the regular synchronization process.
https://www.cisco.com/c/en/us/td/docs/security/firepower/670/configuration/guide/fpmc-config-guide-v67/system_software_updates.html
@Jay: Thank you for your information, we updated Q54!
Hello guys there are only 2 parts for this exam?
Which Cisco FMC report gives the analyst information about the ports and protocols that are related to the configured sensitive network for analysis?
A. Malware Report
B. Host Report
C. Firepower Report
D. Network Report
I think it must be D.
An engineer must add DNS-specific rules to the Cisco FTD intrusion policy. The engineer wants to use the rules currently in the Cisco FTD Snort database that are not already enable but does not want to enable more than are needed.Which action meets these requirements?
A. Change the base policy to Security over Connectivity
B. Change the dynamic state of the rule within the policy
C. Change the rules using the Generate and use recommendations feature
D. Change the rule state within the policy being used
I WANT TO say D not C
The action that meets the requirements of adding DNS-specific rules to the Cisco FTD intrusion policy from the Snort database without enabling more than needed is:
**D. Change the rule state within the policy being used.**
Explanation:
Within the Cisco FTD (Firepower Threat Defense) intrusion policy, individual rules can be enabled or disabled based on the specific needs of the network. To add DNS-specific rules from the Snort database without enabling more than necessary, the engineer can review the available rules in the policy and selectively enable the ones relevant to DNS traffic.
Option A (Change the base policy to Security over Connectivity) doesn’t directly address the need to selectively enable DNS-specific rules; it suggests a broader policy change.
Option B (Change the dynamic state of the rule within the policy) might allow for selective enabling of rules, but it’s not specified how the dynamic state would be adjusted to achieve the desired outcome.
Option C (Change the rules using the Generate and use recommendations feature) could be helpful in identifying relevant rules, but it doesn’t guarantee that only the necessary DNS-specific rules will be enabled.
Therefore, option D is the most appropriate action as it directly involves adjusting the state of individual rules within the policy to add DNS-specific rules from the Snort database without enabling more than needed.
The action that meets the requirements of adding DNS-specific rules to the Cisco FTD intrusion policy from the Snort database without enabling more than needed is:
**D. Change the rule state within the policy being used.**
Explanation:
Within the Cisco FTD (Firepower Threat Defense) intrusion policy, individual rules can be enabled or disabled based on the specific needs of the network. To add DNS-specific rules from the Snort database without enabling more than necessary, the engineer can review the available rules in the policy and selectively enable the ones relevant to DNS traffic.
Option A (Change the base policy to Security over Connectivity) doesn’t directly address the need to selectively enable DNS-specific rules; it suggests a broader policy change.
Option B (Change the dynamic state of the rule within the policy) might allow for selective enabling of rules, but it’s not specified how the dynamic state would be adjusted to achieve the desired outcome.
Option C (Change the rules using the Generate and use recommendations feature) could be helpful in identifying relevant rules, but it doesn’t guarantee that only the necessary DNS-specific rules will be enabled.
Therefore, option D is the most appropriate action as it directly involves adjusting the state of individual rules within the policy to add DNS-specific rules from the Snort database without enabling more than needed.
the answer is D., tested myself in the Lab
There is a dedicated section in the report called
Ports and Protocols Related to Sensitive Network
Are you sure about Question 71 ?
I was not able to pass today…I would say about 30% of the questions on the actual test were from this group of questions. Rest I had never seen.
hello I noticed there is no question 26 but instead from 25 to 27, any reason why
@Landon: It was just a mistake so please ignore it.